题目给了个sh
${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} "${@~}" $'\160'r""$'\151'$@nt"f" %s ' }~~@{$ ") }La?cc87J##@{$ ; } ; }8CC3vD/qX$t/*{$ }~~*{$ "}] "}^@{$" y4R2SV$ "}cIqe[\(\%@{$" "}xk:W=Y2##@{$" [JzbY6E{$" s% ft'"'"'n'"'"''"'"'i'"'"'r\p { ; }*!{$ ] )e#22+)2}8Kr6>#*{$#82*01#3}^*{$(( [$ "};(\S-[\/@{$" "},@{$" ] )71}|$1+d/$_dj/*{$#8+)2#16*1"}xp.{\$Z~[\%@{$"#}~*{$7"1"-(( [$ "@$" "}oMAHn%%@{$" )) )0"1"01"}^@{$"#4}]\oh>-%%@{$+)"a"1#21"-"+l#"1""5"-})\+{\$rMTE%%@{$(( (($ }Omm"\V#*{$ }8z<TPr/*{$ ] ))11"#"2+)"2""#""7""5"-"}qJ)\)\!\{\#/Ije>VU//@{$"-2}_axM-*/*{$#"7""3"(-(-( [$ }f9~U//*{$ }#Jgkvc#@{$ )) )1#}7e[\Trh{\//@{$4+)0#62*0#}*{$"9"(( (($ }S(\{\0)\##@{$ ] )21"}jAVg1-%%@{$""#"5+)"1"1#}*{$4}*{$-*"0"1#"}~~@{$""3"-(( [$ }^^*{$ ] )11#}*!{$"3"+)1*$#93*2#"6"5"@$"(( [$ }0c;x]\^Y//*{$ })\mei/b6B1atD)\//*{$ ] )1"1"0001#2"}fhF`\x/s77vTa[\/@{$"+)0*$#}R"\>(\/RTS8//*{$"6"+l"#"03-(( [$ }^^@{$ )) ))31"#"5+)11#7--00"}&*]\7//@{$"1#2}`\g]\<Roj/}\~(\<Qq/*{$(-(-( (($ }~@{$ )) )"1""#"5}mR&<7r/}\dC!\s*k/*{$3+)i#65-6"1"#}NojyN70T##*{$92}@!{$(( (($ },,*{$ ] )i}Ym5{\y##@{$#}!\a.8/*{$"0"2},,*{$+)01#4+"b"#94}*{$-(( [$ }@{$ }~*{$ )) )52#8+)0#62*0#05(( (($ })\C62X/*{$ }mibf/*{$ )) )"4"2"#"6}~f`\^/@{$1}3NKi^FgW/*{$+)2}="\ulQ;/*{$"#"7}@!{$3-+k#35-(( (($ }*{$ }*{$ ] )i#16+)01#3*11#2}?L7X>/~^MeZH/@{$-(( [$ *$ }@{$ )) )222#3+)11},,@{$#"2"*1"1"#4-(( (($ "}@{$" }*!{$ ] )d#53}e~+uz61###@{$+)0}~~*{$01#2--2"1""#"3(( [$ }~~*{$ )) )j"}^^@{$"#"},@{$"0}~*{$3+)11#4-}ml;.##@{$+"1"#8}"\r"\>cohJ/*{$4(( (($ }*!{$ )) )"a"1"#""1"5+)03#7-e}^^*{$#12-(( (($ "}~@{$" )) ))22"1"#3+)2#"}Y9cefj9%%@{$"41-*$-"y"#84(-(-( (($ }^^@{$ )) )011}~~@{$1},,*{$#2+)"1"#52*11#3-}^^*{$(( (($ }*{$ ] ))0#"1"1+)0#04*0"#"2"},,@{$"1}*!{$(-(-( [$ }~~@{$ )) )43#2"}gC@u/@{$"1+)"1"1}pQCP//*{$#2-}^@{$*01#*$8(( (($ }dlz"\T%%*{$ },h]\rj`\}\/RPQto"\/*{$ )) ))1#2}Vf}\]\Nu##@{$1+)11"#"2--0})\HIZ/*{$#05(-(-( (($ },,*{$ }~~@{$ )) )"a"#"6"3"}TIP]\@V##@{$"+)2}`\.\%Qxt/?:4,/@{$#02-*01#3-}{\Di6HUx@%@{$(( (($ "}~@{$" }34v@##*{$ ] ))11#"5"+)h"}BdoI#@{$"1#1}t*f+fWlA//*{$2+2}~~*{$"1"#},,*{$5-(-(-( [$ };y$!\M8##@{$ )) )1#"7""1"+)0*$"#""1"3*0#5}*{$1"}Rw6a//@{$"(( (($ }Q-Vf9d%%*{$ )) )1},,*{$#15+)0}+lDQf%@{$#"2"*0#74(( (($ }_%$KT9f/iTW~$_/*{$ @$ ] )"m"#3},@{$"3"+)1"1"#2-*0#"5"1(( [$ "},@{$" }TX`\`\%%@{$ ] )"1"1#5"}FE=UU=W./&<"\8l7/@{$"+)0#3*01#3-(( [$ }*{$ }aO;R"\w/9jJF1//*{$ ] )"2"1#"}9uT]\j1f;##@{$""6"+)j#"7"4-"}^^@{$"-b#14-(( [$ }^^*{$ }~~*{$ )) ))1"#"34+)"0"1#}exP"\/TG!\)\T!\?//@{$6+1}*!{$#0}<7V&/*{$6-(-(-( (($ }Mi@S<]\Q#*{$ }^^*{$ ] )2}}\2jz]\G49/#dn>8/*{$2#"}<FTeK&n,//@{$"3"},,@{$"+)1#3-+00}I3cO.O;Z%%@{$"1"#"2"-},*{$(( [$ }B;h_1VnC%%*{$ "}@{$" ] )01}*{$#3+)1#*$8"3"--02#4(( [$ }.\np,/?{\~b03//*{$ "},@{$" )) ))02#4+)"n"#}SPKP8tw##@{$45--1"#"03(-(-( (($ "}@{$" ] ))n"#"14+)s#44+2}@{$2#}~*{$8}7Qq~iq%%*{$(-(-( [$ *$ ] )21"#"4+)n"}~@{$"#}\\@<f$4/*{$45--"1"2"#"3-(( [$ }@{$ }*{$ )) )41#"3"1+)0"#"15*11#"6"(( (($ },,@{$ ] )d#}t_=_//*{$8}ha5]\78/*{$"1"+)01#3"-"*1"}G2T~wh2##@{$""#"64-(( [$ }^^@{$ }.T9P_8Gv//*{$ ] )2"#"73"}$oE?##@{$"+)1},,*{$"1"#}K.o%o$t/uR@fekB#/@{$2-"0""1"#}@bCU%*{$4(( [$ "}3nB?u8fG//@{$" )) )"3""2""#"11"@$"+)0"}~@{$"1#4-+a#5"4"-(( (($ }~y?mRx/BM"\H]\//*{$ "}4^4rR/@{$" ] )"G"#74}~@{$+)2#52}@!{$"-"*a#7"1"(( [$ }@!{$ }~~*{$ ] ))1#84+)31#5+h#03(-(-( [$ }&+?82EU%%*{$ }@!{$ ] )l"#""3"2+)1}~*{$#21*0"}4[\P!\/|Ec{\e/@{$"1}*{$"#"5-(( [$ }:p-c^h+/:r#lsa//*{$ }*{$ )) )00}@!{$1#}BFcS!\%@{$2+)1#"0"6*1#}~~*{$71-(( (($ }~~*{$ }"\&`\QS*%*{$ ] )z"#"44+)11"#""5"-*2#4"2"(( [$ "}^^@{$" }RU*x9!\22/ySk%Ir/@{$ )) )e"#"0"5"+)2#7"2"*"1"1#2"-"(( (($ }*{$ }LNt)\,//@{$ )) ))0#}}\TMHUEV//*{$0}{\^WK!\##*{$6+)11#6-}ahZD^2~/:C,Io\C/*{$-"1"#65-"}H@zpzY8%@{$"(-(-( (($ "}QrL2J\~%%@{$" "}n(\7?)\)\J%%@{$" ] )0"1""#"11+)0#"8"2-11}*{$"#"4(( [$ }(\L-.D:/.41yxK]\//*{$ ] ))21"#"7+)2#24--"f""#"32(-(-( [$ },*{$ }@!{$ ] )22#81}^*{$+)1"1"#4}~*{$"-"*001#}*{$2(( [$ }^^@{$ },,@{$ ] )j},,*{$#"}u7=$6]\/o43H//@{$"2"5"+)1"1""1""#"2-101#2-(( [$ }$Wil##@{$ }l=:G>(\-#@{$ ] ))0#75}~~@{$+)1"#""9"+1"}JZ2I7=&/@{$""1"#}~~*{$3(-(-( [$ ni y4R2SV rof && },,@{$ ) }^*{$ g }^^*{$ y }g$U-b9%@{$ j }*!{$ n }~@{$ *$ u "}(\whfI/@{$" "}@{$" z }RH|<=z##@{$ }~~@{$ '"'"'ax\'"'"'$ }^^@{$ a }~*{$ }dS^Db6G}\%*{$ h }@{$ }^*{$ r "}m&Jk:b?/WBG02h}\_/@{$" \ }T|qd//*{$ }OM`\6.o%@{$ {\ }H%ynnO(\u//*{$ }g8Gv|R~/*{$ _\ }-:zfUz%%*{$ }\ })\#?1{\OK/@{$ *$ i }__b5W:RE//@{$ s }%<Oy{\I//*{$ }"\-iPfz]\g/ug|0w8/*{$ l }L#vh$/{\wLz8/@{$ }60-tI0<%%*{$ 3 "}^@{$" o }euc*##@{$ c }~~*{$ }~~*{$ d }_h)\)\{\/i$V2/@{$ e *$ }(\&`\C?*3%%@{$ ,\ "}@{$" }~@{$ t "},@{$" }^^*{$ #\ }*^RXtV##*{$ m "}@{$" f "},@{$" (=JzbY6E ($" <<< },,*{$ }C0#Y%%*{$ HSAB$ "}|=1SW.//@{$" "@$" ' ${*,} ${@/;mO4/qc~&y} | ${@/a\{oy_BGF/*:wJ} ${@##~@pBeI} "r"""ev ${*~} ${*%K^vf&^3<} ; ${*#SBvLg=k\[} ${*^} )" ${!@}
复制到虚拟机。执行下返回
root@kali:~# ./cmd.sh
dont just run it, dummy
flag应该就在注释里。
开始找sh反混淆的东西
找到了这篇文章
https://www.sohu.com/a/273269706_783648
里面介绍了一个bash调试功能。sh -x
然后就能输出脚本的执行流程。
然后我用sh执行脚本的时候。直接报错。用bash -x也可以
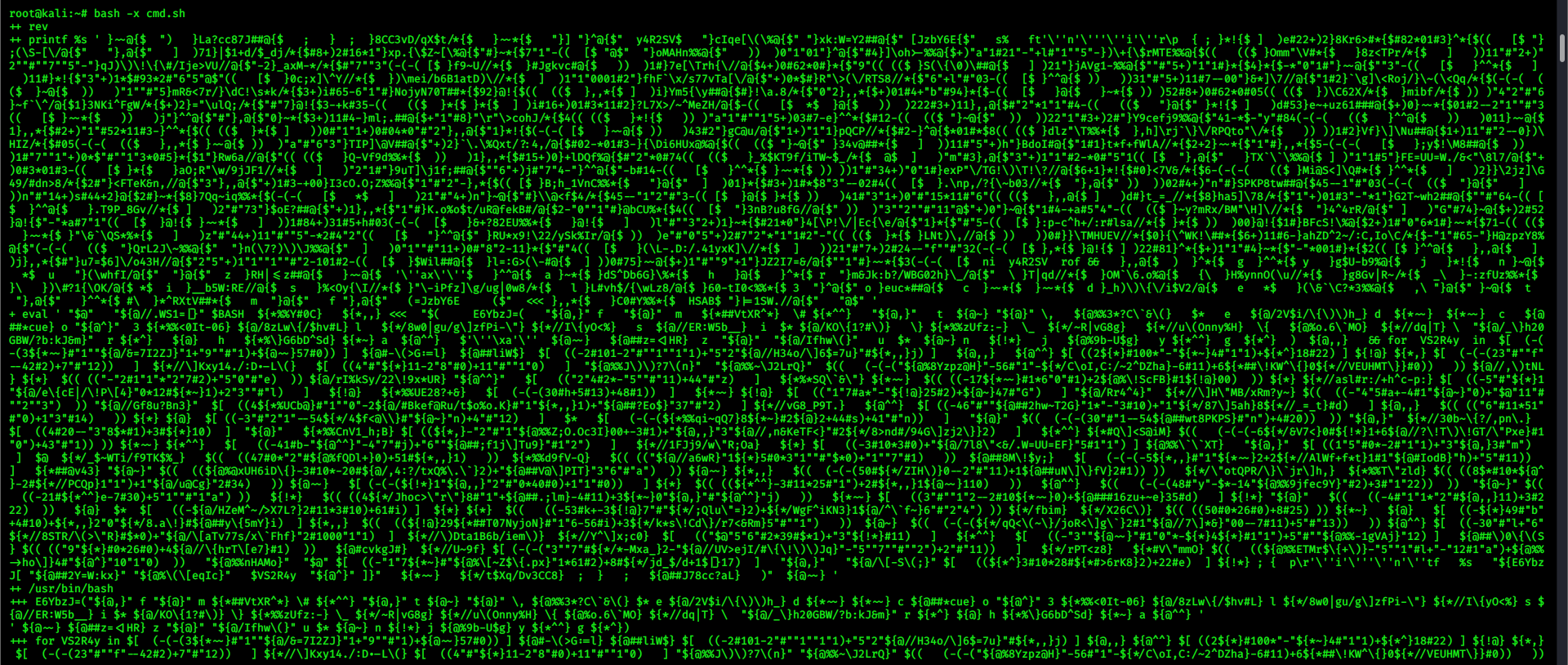
看起来还是很乱。但至少。它输出了脚本每次执行的东西
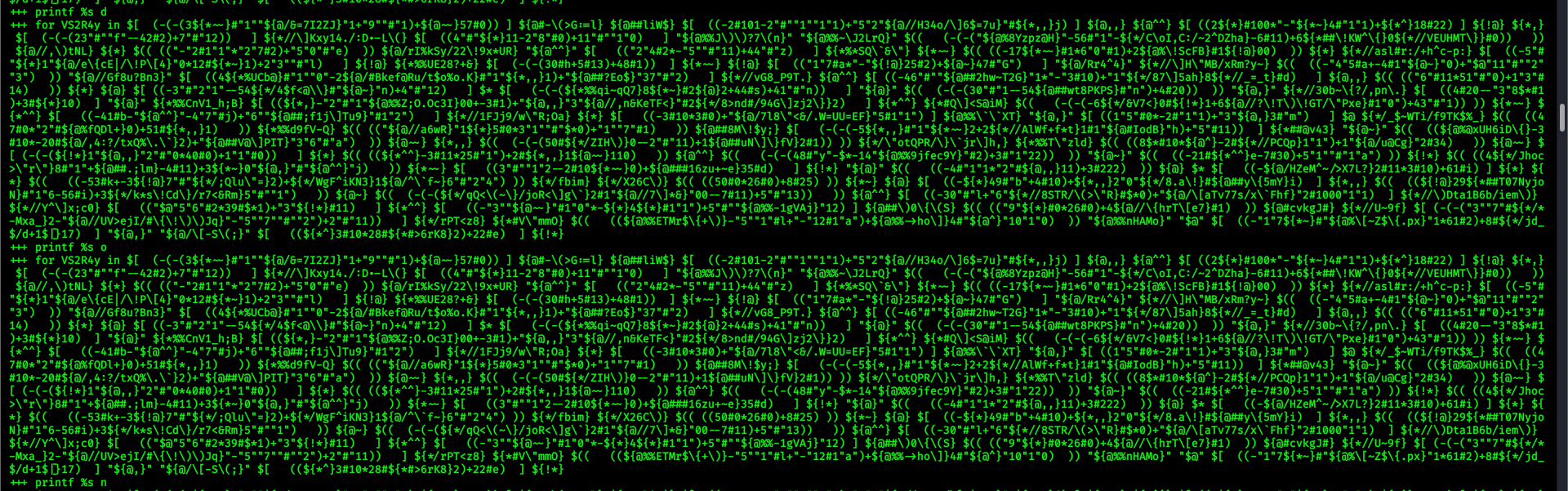
执行了printf %s n
。。还是没思路。把所有内容复制到windows下
windows就很清楚了
flag字样
