解压得到两个文件233.rar和ket.ftm
先从rar开始。直接解压。就一个flag.txt
但是查看16进制。欸还有个233.png

将7A修改为74
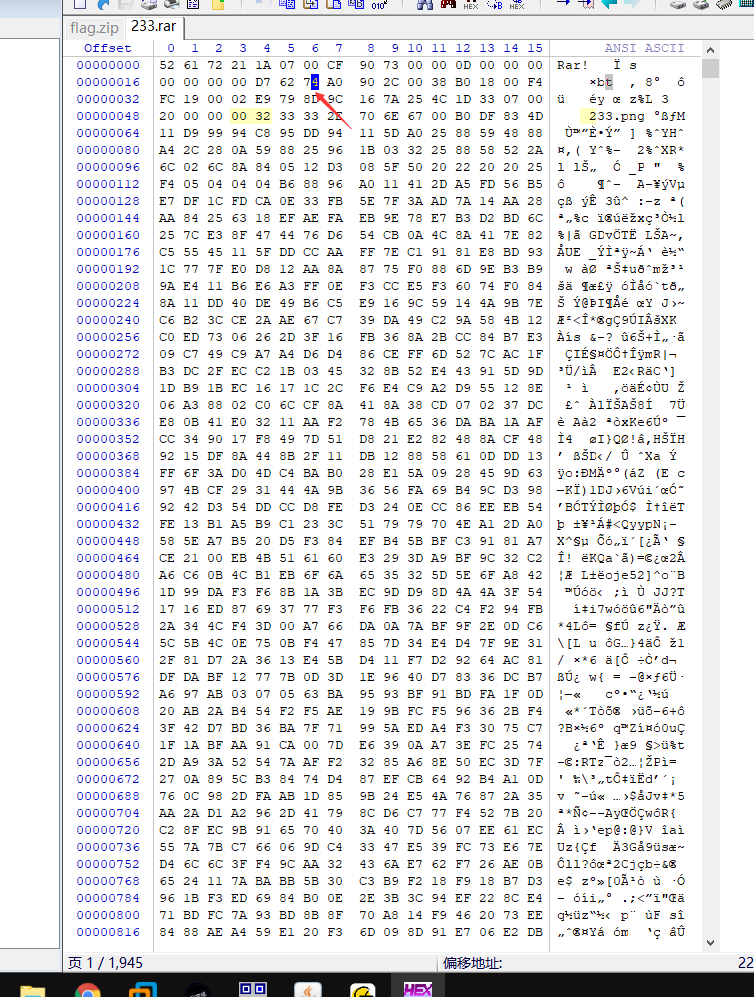
RAR文件格式看大佬博客。有详细讲解
https://yoloyolo.top/archives/85.html
接着。解压出了233.png
用Stegsolve.jar打开
一直点。看到一张二维码

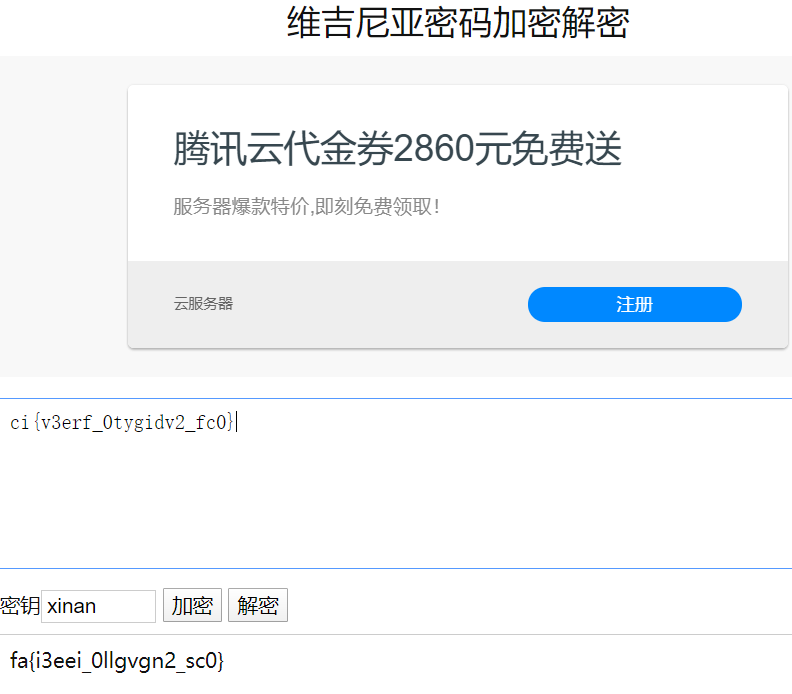
得到ci{v3erf_0tygidv2_fc0}
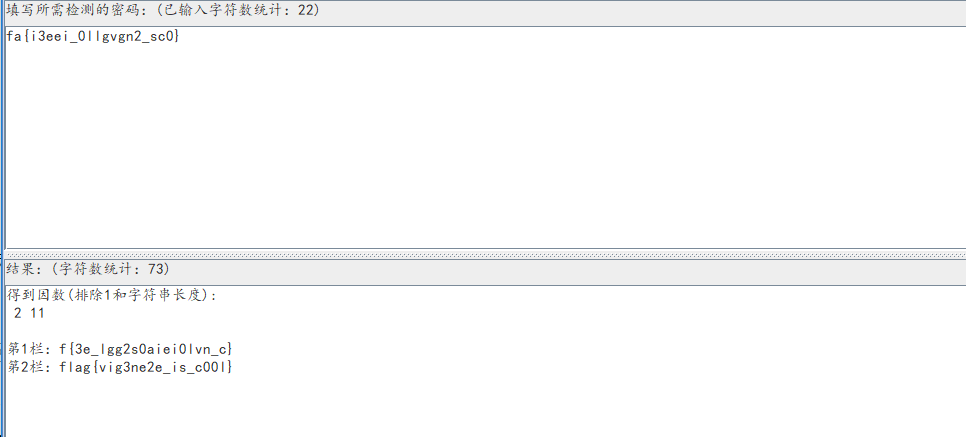
乍一看栏杆密码。但是。不对啊。没a。构成不了flag{xxxx}
。再回去看key.ftm
binwalk分析以下。发现
root@kali:~# binwalk key.ftm
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
34741 0x87B5 Zip archive data, at least v2.0 to extract, compressed size: 4478, uncompressed size: 37254, name: key.pcap
39347 0x99B3 End of Zip archive, footer length: 22
40037 0x9C65 Zip archive data, at least v2.0 to extract, compressed size: 4478, uncompressed size: 37254, name: key.pcap
44643 0xAE63 End of Zip archive, footer length: 22
直接解压出了一个key.pcap
查看。就是USB流量。利用上次的脚本跑
tshark -r key.pcap -T fields -e usb.capdata > usbdata.txt
mappings = { 0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"\"", 0x32:"~", 0x33:";", 0x34:"'", 0x36:",", 0x37:"." }
nums = []
keys = open('usbdata.txt')
for line in keys:
if line[0]!='0' or line[1]!='0' or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0':
continue
nums.append(int(line[6:8],16))
keys.close()
output = ""
for n in nums:
if n == 0 :
continue
if n in mappings:
output += mappings[n]
else:
output += '[unknown]'
print output
得到KEYXINAN
现在就一个KEY。一个字符串。不知道怎么利用。
其实这是维吉尼亚密码(有密钥的凯撒密码)
在线解密下
再通过栅栏密码